Contents
- 1 Abstract
- 2 The Rise of FUNNULL—A Global Cybercrime Nexus Facilitating Financial Fraud, Cryptojacking, and Supply Chain Attacks
- 3 What is FUNNULL?
- 4 The Silent Manipulation: How FUNNULL’s CDN Empowers Global Financial Deception and Cyber Fraud
- 5 The Corporate Veil of FUNNULL: Unmasking the Nexus Between Cybercrime, Gambling Syndicates, and Financial Laundering
- 6 The Globalized Nexus of Casino Junkets, Money Laundering, and Transnational Financial Crime
- 7 The Vancouver Model: A Transnational Blueprint for Casino-Based Money Laundering and Financial Crime
- 8 The Digital Architecture of Financial Crime: Suncity Group’s Integration with FUNNULL and Cryptocurrency Laundering Networks
- 9 The Digital Exploitation of Online Gambling: A Conduit for Money Laundering and Transnational Financial Crime
- 10 Cryptocurrency-Integrated Money Laundering: The Rise of Points Running Syndicates and Motorcade Networks
- 10.0.1 The Evolution of Points Running Syndicates: A Distributed Laundering Network
- 10.0.2 Motorcade Networks and High-Speed Cryptocurrency Laundering
- 10.0.3 China’s Cryptocurrency Ban and the Migration of Laundering Networks
- 10.0.4 Cryptocurrency-Based Money Laundering and Regulatory Challenges
- 10.0.5 The Role of Online Gambling Platforms in Cryptocurrency Laundering
- 10.0.6 Countering Cryptocurrency-Enabled Money Laundering
- 11 The Proliferation of USDT-Based Money Laundering Networks and the Convergence of Cybercrime, Online Gambling, and Human Trafficking
- 12 The Retail Phishing Ecosystem on FUNNULL: Unmasking a Coordinated Cybercrime Campaign
- 12.0.1 The Targeted Retail Brands and Their Exploitation
- 12.0.2 Technical Analysis of FUNNULL-Hosted Phishing Infrastructure
- 12.0.3 Pig Butchering and Investment Fraud Components
- 12.0.4 Operational Security Measures and Unpublished Findings
- 12.0.5 Strategic Countermeasures and Recommended Mitigation Steps
- 13 Polyfill.io Supply Chain Compromise: A Systemic Cybersecurity Threat
- 13.0.1 Exploitation of a Trusted Resource
- 13.0.2 Widespread Global Impact with a Focus on Europe and Italy
- 13.0.3 Infrastructure Laundering: The Role of FUNNULL in Expanding Attack Vectors
- 13.0.4 Google and Industry Response: Emergency Mitigation Measures
- 13.0.5 Strategic Cybersecurity Recommendations for Italy
- 14 FUNNULL’s Exploitation of CDN Infrastructure: An Advanced Analysis of Cybercriminal Mechanisms
- 15 Triad Nexus: Advanced Indicators of Future Attacks and Infrastructure Mapping
- 16 The Expansion of FUNNULL’s CDN: An Unprecedented Cyber Infrastructure in Europe
- 17 FUNNULL’s Impact on Europe with a Focus on Italy: A Verified and Detailed Analysis
- 18 The Deepening Threat of FUNNULL: Cryptojacking, Supply Chain Attacks, and the Subversion of Global Cybersecurity
- 18.1 Connecting the Dots: How FUNNULL Orchestrated a Cryptojacking Campaign Against USAID
- 18.2 Why FUNNULL’s Cryptojacking Campaign Is More Than Just Financial Theft
- 18.3 FUNNULL’s Infrastructure: A Growing Cybersecurity Catastrophe
- 18.4 The Urgent Need for a Coordinated Global Response Against FUNNULL
Abstract
As the digital economy expands, so too does the infrastructure that enables large-scale cybercrime, fraud, and transnational financial manipulation. At the forefront of this evolution is FUNNULL, a China-linked Content Delivery Network (CDN) that has transformed into one of the most formidable enablers of digital crime worldwide. No longer limited to traditional malicious hosting, FUNNULL operates as a cybercriminal superstructure, leveraging high-profile cloud computing services such as Amazon Web Services (AWS) and Microsoft Azure to sustain bulletproof hosting, financial scams, money laundering, and cryptojacking operations at an unprecedented scale.
Recent forensic analyses have revealed that FUNNULL’s infrastructure supports a vast network of algorithmically generated fraudulent domains, sophisticated online trading scams, and illicit gambling syndicates, many of which impersonate legitimate financial institutions. With over 200,000 domains linked to FUNNULL, its ecosystem has defrauded investors across Europe and Asia while seamlessly integrating into underground money laundering networks. Blockchain investigations further indicate that FUNNULL plays a central role in laundering illicit funds through stablecoins, particularly USDT (Tether), facilitating financial crimes on a massive scale.
Perhaps most concerning, FUNNULL’s infiltration into critical software supply chains was demonstrated in its takeover of polyfill.io, a widely used JavaScript library embedded in over 110,000 websites worldwide. By injecting malicious code into this legitimate library, FUNNULL weaponized software dependencies to conduct a large-scale supply chain attack, implanting malware, harvesting user credentials, and redirecting traffic to fraudulent portals under its control. The attack exposed thousands of commercial and government organizations to severe cybersecurity risks, proving that FUNNULL’s reach extends beyond financial fraud into direct cyber-espionage tactics.
Moreover, FUNNULL’s infrastructure has been linked to cryptojacking operations targeting U.S. federal agencies, including the 2024 attack on the U.S. Agency for International Development (USAID). In this incident, password spray attacks and cloud resource hijacking through Microsoft Azure enabled attackers to mine cryptocurrency using government-funded computing resources, incurring over $500,000 in unauthorized cloud expenses. The methodology closely aligns with FUNNULL’s tactics of leveraging high-reputation cloud services to execute persistent cybercriminal operations while evading detection.
Despite global enforcement efforts, FUNNULL continues to expand its cybercriminal empire, embedding itself deeper into global infrastructure and exploiting weaknesses in cloud security, regulatory frameworks, and financial oversight. The CDN’s reliance on bulletproof hosting, algorithmic domain generation, and AI-driven fraud schemes underscores a new era of cybercrime, where infrastructure, finance, and digital deception converge to form an unparalleled transnational threat.
Given the scale and sophistication of FUNNULL’s operations, dismantling this cybercriminal network will require coordinated international cybersecurity efforts, cross-sector intelligence sharing, and stricter regulatory controls over cloud-hosted infrastructure. As FUNNULL solidifies its position as a central node in the global cybercrime ecosystem, failing to act decisively will allow this clandestine network to further entrench itself into the very fabric of the digital economy, facilitating financial crime, cyber-espionage, and supply chain compromises on an unprecedented scale.
The Rise of FUNNULL—A Global Cybercrime Nexus Facilitating Financial Fraud, Cryptojacking, and Supply Chain Attacks
As the digital economy expands, a parallel, insidious infrastructure has taken root—one that exists in the murky underworld of cybercrime, fraud, and transnational financial manipulation. This vast, elusive ecosystem is fueled by FUNNULL, a China-linked Content Delivery Network (CDN) that has rapidly evolved into one of the most formidable enablers of digital crime worldwide. By leveraging high-profile cloud computing services such as Amazon Web Services (AWS) and Microsoft Azure, FUNNULL has cemented itself as a shadow network, hosting and facilitating illicit activities at an unprecedented scale. Beyond merely providing hosting services, FUNNULL’s infrastructure operates as a highly sophisticated cybercriminal facilitator, a command-and-control nexus that coordinates complex financial scams, bulletproof hosting, and transnational laundering networks designed to bypass regulatory scrutiny and law enforcement intervention.
The implications of FUNNULL’s operations stretch far beyond traditional cybercrime. What sets it apart is its seamless integration with algorithmically generated domains, an extensive network of fraudulent trading applications, and a direct connection to illicit gambling syndicates. The latest forensic analysis into FUNNULL’s digital footprint has revealed that nearly 95% of the 200,000 domains under its control are generated through Domain Generation Algorithms (DGAs), a method that cybercriminal enterprises use to maintain persistent control over their illicit operations. Unlike conventional DGA-based malware networks, which generate random domain names to evade takedowns, FUNNULL employs a more sophisticated approach—mirroring legitimate corporate branding, financial institutions, and trading platforms in a manner that allows fraudulent sites to blend seamlessly with genuine counterparts.
Among the most striking discoveries of recent investigations is the FUNNULL-backed proliferation of fraudulent trading platforms and online investment scams, many of which impersonate globally recognized financial institutions. These deceptive platforms have been instrumental in defrauding unsuspecting investors, particularly in Europe and Asia, where cryptocurrency and forex trading scams have witnessed exponential growth. A forensic review of FUNNULL’s infrastructure has linked the CDN to high-profile fraudulent trading platforms, including replicas of CME Group, Binance, and regional financial firms. By employing DNS obfuscation techniques, these fraudulent platforms remain online for prolonged periods, targeting victims through highly convincing advertising campaigns and social media promotions before swiftly disappearing—only to be replaced by near-identical copies hosted under new FUNNULL-generated domains.
The rapid growth of FUNNULL’s influence in financial fraud is further exacerbated by its connections to transnational money laundering networks. An in-depth examination of Telegram channels linked to FUNNULL’s infrastructure uncovered numerous references to underground financial operations, including illicit remittance services and cryptocurrency-based laundering channels. This suggests that FUNNULL is not only facilitating cybercrime but also actively embedding itself into the global financial system, enabling the seamless flow of illicit funds through shadow banking networks, stablecoin-based laundering schemes, and unregulated cryptocurrency exchanges. Notably, FUNNULL-linked operations have displayed a strong preference for Tether (USDT), the stablecoin frequently associated with illicit financial activities across Asia and the Middle East. Analysis of blockchain transactions reveals that thousands of FUNNULL-associated scam websites prominently feature Tether promotions, further solidifying the theory that this CDN serves as an enabler for laundering operations on a massive scale.
Beyond financial crime, FUNNULL’s infrastructure also plays a crucial role in the proliferation of illegal online gambling networks. Researchers monitoring the CDN’s activity identified over 40,000 mirrored gambling domains, most of which were structured to target Chinese and Southeast Asian markets. These platforms are designed to evade regulatory oversight by frequently rotating domain registrations, employing dynamic subdomains, and hosting on high-reputation IP spaces leased from compromised or unregulated providers. The majority of these gambling sites have been found to operate under branding associated with Suncity Group and other major operators, raising questions about the potential collaboration between organized crime syndicates and FUNNULL’s shadow infrastructure.
The evolution of FUNNULL’s infrastructure took a darker turn in 2024 when cybersecurity analysts uncovered its acquisition of polyfill.io, a widely used JavaScript library integrated into more than 110,000 websites worldwide. By injecting malicious scripts into polyfill.io’s legitimate codebase, FUNNULL executed a large-scale supply chain attack that compromised thousands of commercial and government organizations. This unprecedented exploit enabled cybercriminals to harvest user credentials, implant malware, and redirect unsuspecting visitors to fraudulent portals under FUNNULL’s control. The ability to weaponize a widely trusted software component underscored the growing sophistication of FUNNULL’s operations and its intent to blur the lines between legitimate digital infrastructure and cybercriminal networks.
Further complicating efforts to dismantle FUNNULL’s activities is its reliance on bulletproof hosting, a tactic employed by malicious service providers that refuse to comply with takedown requests. Unlike traditional hosting services, which cooperate with law enforcement agencies to remove illegal content, FUNNULL’s CDN has built a reputation for aggressively resisting domain suspensions and IP blacklisting. This defiance is underscored by the group’s own cryptic statement: “Behind a cute name, there is a violent beast standing.” This phrase, found within FUNNULL’s promotional materials, serves as a stark acknowledgment of its true nature—a network designed not only to evade detection but to thrive within the shadows of the digital world.
Despite mounting pressure from international law enforcement agencies, FUNNULL continues to expand its reach, finding new ways to infiltrate global digital infrastructure. The sustained presence of FUNNULL-linked domains on cloud providers such as Microsoft and Amazon indicates a persistent failure in automated threat detection and domain abuse mitigation. Recent analyses suggest that nearly 40% of FUNNULL’s Point of Presence (PoP) servers are allocated to AS8075 (Microsoft Corporation) and AS16509 (Amazon.com Inc.), demonstrating the scale at which major cloud platforms are being exploited. This exploitation of reputable infrastructure has allowed FUNNULL to maintain uninterrupted access to the digital economy, despite numerous takedown attempts and ongoing security measures by affected organizations.
The future of FUNNULL’s operations remains uncertain, but one fact is abundantly clear: this is not merely a transient cybercrime entity but rather an evolving ecosystem that continuously adapts to countermeasures imposed by global cybersecurity efforts. As the digital battlefield grows increasingly complex, security professionals, regulatory bodies, and financial institutions must collaborate on a scale never before seen to combat the multifaceted threats posed by this clandestine network. The rise of FUNNULL signals the emergence of a new paradigm in cybercrime—one where infrastructure, finance, and digital deception converge to form an unparalleled global threat.
What is FUNNULL?
FUNNULL is a China-linked Content Delivery Network (CDN) . A CDN is typically a service that helps websites deliver content faster by caching it on servers closer to users. For example, if you visit a website hosted in the U.S., but you’re in Europe, a CDN will serve the website’s content from a server in Europe to make it load faster.
However, FUNNULL is not using its CDN for legitimate purposes. Instead, it’s exploiting major cloud providers like AWS and Azure to host malicious websites (e.g., phishing sites, fake gambling platforms, investment scams). These malicious websites are used to steal money, personal information, or spread malware.
How Does FUNNULL Exploit AWS and Azure?
Renting IP Addresses
- FUNNULL rents IP addresses from AWS and Azure. These IP addresses are like “addresses” for servers on the internet. For example:
- AWS gives you an IP address like
54.239.176.1when you rent a server. - FUNNULL uses these IPs to host their malicious websites.
- AWS gives you an IP address like
Using Stolen or Fraudulent Accounts
- FUNNULL doesn’t use real accounts. They create fake accounts or steal identities to sign up for AWS and Azure services. This makes it harder for AWS and Azure to detect who is behind these accounts.
- Example: FUNNULL might use stolen credit card information or fake email addresses to create accounts.
Mapping IP Addresses to Malicious Domains
- Once FUNNULL has the IP addresses, they link them to fraudulent domains (website addresses) using DNS CNAME records .
- A CNAME record is like a nickname for a domain. For example:
- The domain
fake-bwin.com(a phishing site pretending to be Bwin, a gambling company) can be linked to the IP address54.239.176.1.
- The domain
- FUNNULL uses Domain Generation Algorithms (DGAs) to create thousands of fake domains automatically. For example:
fake-bwin1.com,fake-bwin2.com,fake-bwin3.com, etc.
- A CNAME record is like a nickname for a domain. For example:
Hosting Malicious Websites
- These fake domains are used to host malicious websites , such as:
- Phishing sites : Fake login pages for companies like eBay or Chanel to steal user credentials.
- Fake gambling sites : Pretending to be legitimate gambling platforms to scam users out of money.
- Investment scams : Promising high returns to trick people into sending money.
Why Can’t AWS and Azure Just Ban Them?
AWS and Azure try to stop FUNNULL, but it’s not easy because:
Rapid Cycling of IP Addresses
- FUNNULL constantly changes the IP addresses they use. Even if AWS bans one set of IPs, FUNNULL quickly rents new ones.
- Example: AWS bans
54.239.176.1, but FUNNULL immediately starts using54.239.176.2.
- Example: AWS bans
Blending with Legitimate Traffic
- FUNNULL’s malicious websites blend in with legitimate traffic. AWS and Azure host millions of websites, so it’s hard to distinguish between good and bad ones.
- Example: If AWS blocks all traffic to
54.239.176.1, it might accidentally block a legitimate website sharing the same server.
- Example: If AWS blocks all traffic to
Weak Account Verification
- FUNNULL creates fake accounts using stolen identities or fraudulent information. AWS and Azure’s account verification processes aren’t perfect, so FUNNULL slips through.
- Example: FUNNULL uses a stolen credit card to create an AWS account, and AWS doesn’t detect it until later.
Global Scale
- FUNNULL operates globally, making it hard for AWS and Azure to coordinate with law enforcement in different countries.
- Example: FUNNULL rents IPs in the U.S., but the criminals behind it are based in China, making legal action difficult.
Example of Fraud: Fake Bwin Gambling Website
Let’s walk through a real-world fraud example to show how FUNNULL works:
Step 1: Creating a Fake Domain
- FUNNULL registers a domain like
fake-bwin.com(pretending to be the legitimate gambling site Bwin). - They use a Domain Generation Algorithm (DGA) to create variations like
fake-bwin1.com,fake-bwin2.com, etc.
Step 2: Renting an IP Address
- FUNNULL rents an IP address (
54.239.176.1) from AWS using a stolen account. - They link this IP address to the domain
fake-bwin.comusing a CNAME record .
Step 3: Hosting the Malicious Website
- FUNNULL sets up a fake gambling website on
fake-bwin.com. The site looks identical to the real Bwin website, but it’s designed to steal money.- Example: Users deposit money into the fake site, thinking they’re playing on Bwin. However, the money goes directly to FUNNULL’s bank accounts.
Step 4: Spreading the Link
- FUNNULL spreads the link to
fake-bwin.comthrough phishing emails, social media ads, or search engine ads.- Example: You receive an email saying, “Win big at Bwin! Click here to play now.” The link takes you to
fake-bwin.com.
- Example: You receive an email saying, “Win big at Bwin! Click here to play now.” The link takes you to
Step 5: Stealing Money
- When users deposit money on
fake-bwin.com, FUNNULL steals it. Since the website is hosted on AWS, it appears legitimate, making it harder for users to suspect fraud.
Why Is This So Hard to Stop?
- Speed of Operations
- FUNNULL can rent new IPs and create new domains faster than AWS and Azure can detect and ban them.
- Use of Reputable Cloud Providers
- Because FUNNULL uses AWS and Azure, their websites appear trustworthy. Many security systems don’t block traffic from AWS or Azure because they assume it’s safe.
- Sophisticated Techniques
- FUNNULL uses advanced techniques like DGAs and DNS CNAME chains to hide their activities. This makes it hard for cybersecurity tools to track them.
What Can Be Done to Stop FUNNULL?
- Better Account Verification
- AWS and Azure need stricter identity checks to prevent FUNNULL from creating fake accounts.
- Real-Time Monitoring
- Use AI and machine learning to detect suspicious behavior, like rapid IP cycling or unusual DNS configurations.
- Collaboration Between Companies
- AWS, Azure, and cybersecurity firms like Silent Push should share information about FUNNULL’s activities to take coordinated action.
- Law Enforcement Involvement
- Governments and law enforcement agencies need to work together to shut down FUNNULL’s operations globally.
FUNNULL is exploiting AWS and Azure by renting IP addresses, linking them to fake domains, and hosting malicious websites like phishing sites and fake gambling platforms. They use stolen accounts and advanced techniques to avoid detection. While AWS and Azure try to stop them, FUNNULL’s speed, scale, and sophistication make it difficult.
Fraud Example Recap :
- FUNNULL creates a fake gambling site (
fake-bwin.com) hosted on AWS. - Users think they’re playing on Bwin but lose money to FUNNULL.
- AWS struggles to ban FUNNULL because they constantly change IPs and blend with legitimate traffic.
The Silent Manipulation: How FUNNULL’s CDN Empowers Global Financial Deception and Cyber Fraud
A hidden digital empire thrives beneath the surface of global internet infrastructure—an insidious, highly sophisticated operation that facilitates financial deception on an unprecedented scale. FUNNULL, an advanced China-linked Content Delivery Network (CDN), has evolved far beyond its original cybercriminal ecosystem, mutating into a robust mechanism for fraudulent trading applications, illicit financial schemes, and deception networks that continuously reshape their methodologies to evade detection. Silent yet omnipresent, FUNNULL has infiltrated the core of digital finance, exploiting the very foundations of global connectivity to execute an intricate matrix of financial fraud. This is not merely a network—it is a living, evolving entity designed to perpetuate transnational financial exploitation while shielding its perpetrators from the consequences of their actions.
Emerging forensic evidence illustrates a pattern of sustained deception fueled by FUNNULL’s extensive infrastructure, which enables the seamless replication and dissemination of fraudulent trading applications. Investigations into historical DNS records reveal that over 200,000 domains linked to FUNNULL’s hosting framework exhibit algorithmic generation patterns indicative of high-frequency domain cycling. This allows threat actors to generate and deploy thousands of fake trading apps that impersonate legitimate financial institutions, capitalizing on brand recognition to lure unsuspecting investors into sophisticated scam operations. By integrating domain generation algorithms (DGAs) with rapidly shifting CNAME records, FUNNULL ensures the persistent existence of fraudulent applications, mitigating the risk of domain takedown efforts and legal enforcement.
The global financial landscape is increasingly plagued by fake investment schemes leveraging FUNNULL’s CDN infrastructure. Within this extensive ecosystem, well-established financial brands such as the Australian Securities Exchange (ASX), Coinbase, CoinSmart, eToro, and Nasdaq have been consistently impersonated, with fraudsters constructing hyper-realistic digital facades that siphon funds from unsuspecting investors. The staggering expansion of these deceptive platforms, orchestrated through FUNNULL’s rapid deployment methodology, has led to an explosion in financial crime, with estimated losses surpassing tens of billions of euros worldwide. The deployment of highly targeted phishing mechanisms, often augmented by AI-driven social engineering strategies, ensures that victims perceive fraudulent platforms as legitimate investment opportunities, rendering them particularly vulnerable to manipulation.
A deeper dive into FUNNULL’s network structure unveils a troubling alliance between cybercriminal syndicates and the infrastructure providers that inadvertently facilitate their operations. Analysis of FUNNULL’s autonomous system number (ASN) distributions indicates that nearly 40% of its PoPs are hosted on Microsoft (AS8075) and Amazon (AS16509), raising significant concerns about the role of major cloud platforms in sustaining this vast web of financial deception. The deliberate obfuscation of ownership records, coupled with the use of nested shell corporations, further complicates attribution efforts, allowing cybercriminals to maintain uninterrupted access to the world’s most powerful digital infrastructure while effectively nullifying efforts by regulatory authorities to curb their activities.
Beyond traditional financial fraud, FUNNULL’s hosting capabilities have proven invaluable for large-scale money laundering operations. Recent investigations into Telegram-based financial crime networks have uncovered direct links between FUNNULL-backed trading scams and underground cryptocurrency laundering channels, where illicitly obtained funds are systematically funneled through anonymized digital assets. These transactions, often conducted in Tether (USDT), provide a virtually untraceable medium for cross-border capital movement, further reinforcing the role of FUNNULL’s CDN as an essential enabler of transnational financial crime. By facilitating instantaneous asset transfers across international jurisdictions, FUNNULL empowers money launderers to bypass traditional banking controls, enabling a new era of decentralized, algorithmically optimized financial crime.
Compounding the risks associated with FUNNULL’s cyber ecosystem is its involvement in the proliferation of counterfeit job recruitment networks—a rapidly expanding sector of cyber fraud that exploits professional platforms to recruit unsuspecting individuals into fraudulent trading schemes. Leveraging deepfake technology and AI-generated personas, these fake recruitment initiatives provide an additional layer of legitimacy to fraudulent investment platforms, ensuring a steady influx of new victims into FUNNULL’s operational framework. Once onboarded, victims are manipulated into transferring funds to seemingly credible trading platforms, only to discover that their investments have been funneled into a complex web of untraceable digital accounts operated by organized cybercriminal syndicates.
Further research into FUNNULL’s domain clusters has revealed alarming insights into the sheer scale of its deception tactics. Analyzing current and historical CNAME resolutions associated with FUNNULL’s network, cybersecurity analysts have uncovered a timeline of domain migrations designed to obfuscate fraudulent operations. From early CNAME associations with vk6a2rmn-u.funnull[.]vip in 2022, shifting towards 6ce0a6db.u.fn03[.]vip in 2024, the relentless evolution of FUNNULL’s domain structure underscores a calculated approach to sustained deception. The ability to seamlessly transition between hosting frameworks without disrupting fraudulent operations exemplifies the level of resilience engineered into FUNNULL’s infrastructure, demonstrating a refined capability for subverting traditional cybersecurity countermeasures.
Efforts to counteract FUNNULL’s impact are hindered by the deliberate opacity of its infrastructure and the continued exploitation of high-trust hosting environments. Unlike conventional cybercriminal networks that rely on compromised servers or low-tier hosting providers, FUNNULL’s deep integration within major cloud ecosystems complicates takedown efforts, necessitating advanced threat intelligence collaboration between private cybersecurity firms, governmental agencies, and financial institutions. The growing urgency of this issue has prompted increased scrutiny of FUNNULL’s presence within global cybersecurity frameworks, yet the lack of direct attribution mechanisms continues to pose significant challenges in effectively dismantling its network.
The next phase of combating FUNNULL’s influence requires a radical shift in the approach to financial cybercrime enforcement. Advanced machine-learning-driven anomaly detection systems, coupled with real-time blockchain forensic analysis, must be leveraged to trace illicit financial flows and disrupt fraudulent transactions at the source. Enhanced regulatory oversight of cloud service providers is also critical, ensuring that FUNNULL’s operations cannot continue unchecked within legitimate hosting environments. The deployment of targeted legal frameworks that criminalize the facilitation of cyber fraud through digital infrastructure partnerships will be instrumental in dismantling the core enablers of this vast deception network.
As FUNNULL continues its rapid expansion, the implications of its existence extend far beyond traditional cybercrime. What began as a relatively obscure CDN hosting fraudulent trading applications has transformed into a vast, algorithmically driven financial crime syndicate—one that is reshaping the global cybersecurity threat landscape. The necessity of a coordinated, multi-jurisdictional response to FUNNULL’s operations is more pressing than ever, as the future of financial security hinges upon the ability to dismantle this highly adaptive, deeply entrenched cybercriminal infrastructure.
The Corporate Veil of FUNNULL: Unmasking the Nexus Between Cybercrime, Gambling Syndicates, and Financial Laundering
Beneath the surface of the global digital economy, a clandestine network flourishes—one that extends far beyond traditional cybercriminal activity, embedding itself within regulated financial systems and leveraging high-trust infrastructure to perpetuate large-scale financial deception. FUNNULL, a notorious China-linked Content Delivery Network (CDN), has emerged as the backbone of an elaborate scheme that intersects fraudulent digital platforms, illicit gambling networks, and sophisticated money laundering syndicates. This is not merely a case of criminal opportunism; rather, it represents the calculated engineering of a shadow infrastructure designed to manipulate the flow of digital capital while obscuring the true identity of its beneficiaries.
Recent forensic investigations into FUNNULL’s corporate branding reveal a multifaceted operational model that caters explicitly to organizations seeking anonymity, mass domain hosting, and resilient obfuscation mechanisms. The entity markets itself through multiple URLs, including funnull[.]com and funnull[.]io, both of which act as entry points into a labyrinthine ecosystem of high-speed hosting services, bulletproof infrastructure, and bulk domain management. Historical snapshots of FUNNULL’s parent entity, ACB Group—previously hosted at acb[.]bet—offer a glimpse into a carefully curated corporate facade, one that publicly affiliates itself with sports betting and online gaming ventures while discreetly facilitating global financial fraud. Although the original corporate site has since been taken offline, archived records provide damning evidence of FUNNULL’s strategic alliances with high-risk industries, particularly within the gambling and offshore banking sectors.
An even more alarming dimension of FUNNULL’s operations emerges upon analysis of its infrastructure deployment within China. Data retrieved from HUIDU, an intelligence repository for the online gaming industry, confirms that FUNNULL maintains over 30 active data centers within mainland China, a jurisdiction infamous for its stringent regulatory oversight of financial transactions and digital enterprises. Despite Beijing’s aggressive crackdown on unauthorized financial networks, FUNNULL has successfully entrenched itself within the country’s digital economy, utilizing high-security automated server facilities to facilitate a seamless flow of illicit capital across borders. This raises critical questions about regulatory blind spots and potential state-aligned interests that may be shielding FUNNULL from disruption, allowing it to thrive despite its well-documented association with illicit financial operations.
Further analysis of FUNNULL’s pricing model exposes a highly unorthodox business structure, one that is explicitly tailored to organizations engaged in bulk domain manipulation and obfuscation tactics. Unlike conventional CDN providers, which prioritize legitimate content delivery optimization, FUNNULL’s pricing tiers are uniquely structured to incentivize mass domain registrations—offering 80% discounted rates for clients managing 50 domains or more. This configuration is particularly advantageous to cybercriminal enterprises that rely on Domain Generation Algorithms (DGAs) to create thousands of fraudulent domains, ensuring their operations remain resilient against domain blacklisting and law enforcement takedown requests. By integrating high-frequency domain cycling with an advanced DNS obfuscation framework, FUNNULL has effectively nullified traditional cybersecurity countermeasures, enabling its clients to operate at an unprecedented scale of deception.
One of the most consequential revelations from recent research is the deep entanglement between FUNNULL and Suncity Group, a now-defunct Macau-based junket operator with a documented history of transnational financial crimes. Silent Push investigators uncovered that thousands of online gambling websites hosted on FUNNULL’s infrastructure prominently feature Suncity Group’s branding, raising concerns about potential collusion between the CDN and the remnants of Suncity’s illicit financial empire. This connection is particularly damning given that Suncity’s former CEO, Alvin Chau, was sentenced to 18 years in prison in 2023 for his role in a vast money laundering operation that funneled illicit funds through underground banking networks, laundering an estimated $40 billion USD over the span of a decade.
The United Nations Office on Drugs and Crime (UNODC) has since linked Suncity Group’s financial apparatus to Lazarus Group, a North Korean state-sponsored cybercrime syndicate known for executing some of the most devastating financial cyberattacks in modern history. Among the most striking elements of this revelation is that Lazarus Group reportedly laundered $19 million USD through Suncity-affiliated networks, leveraging online gambling platforms as a conduit for illicit cryptocurrency transactions. A forensic comparison between the UNODC’s financial intelligence reports and Silent Push’s dataset on FUNNULL-hosted domains reveals staggering overlaps in site infrastructure, suggesting that elements of Suncity’s former digital footprint have been repurposed under FUNNULL’s umbrella to continue facilitating financial crimes under a new guise.
A particularly damning piece of evidence supporting FUNNULL’s involvement in financial crime emerges through the forensic examination of historical CNAME records linked to its infrastructure. Silent Push analysts identified a timeline of systematic domain migrations, beginning with vk6a2rmn-u.funnull[.]vip in early 2022, shifting to vk6a2rmn-u.funnull01[.]vip by mid-2023, and eventually transitioning to 6ce0a6db.u.fn03[.]vip in 2024. This meticulously structured migration strategy reflects a deliberate attempt to evade domain-based blocking mechanisms while maintaining operational continuity for illicit financial operations.
Moreover, FUNNULL’s capacity to remain operational despite global enforcement efforts underscores its reliance on bulletproof hosting methodologies, a tactic commonly employed by cybercriminal enterprises seeking resilience against legal takedown requests. Unlike legitimate CDN providers, which comply with international regulatory frameworks, FUNNULL has actively resisted compliance measures, as evidenced by its lack of an official takedown request process. This deliberate omission strongly suggests that FUNNULL operates under a hostile compliance posture, positioning itself as an enabler of financial fraud rather than a conventional content distribution provider.
Complicating matters further, Silent Push’s real-time DNS resolution data indicates that FUNNULL’s hosting infrastructure has infiltrated Tier 1 cloud providers, with nearly 40% of its Points of Presence (PoPs) residing within Microsoft (AS8075) and Amazon (AS16509). The presence of FUNNULL nodes within these high-trust cloud environments highlights a systemic failure in automated threat detection mechanisms, allowing illicit financial operations to persist undetected within the world’s most reputable internet service providers. This raises urgent concerns about the efficacy of automated abuse monitoring, as traditional cloud governance policies have demonstrably failed to mitigate FUNNULL’s expansion within critical global infrastructure.
The sheer scale of FUNNULL’s impact demands a radical reevaluation of cybersecurity countermeasures. Future mitigation strategies must integrate behavioral analytics, blockchain forensic tracing, and advanced AI-driven domain attribution models to disrupt FUNNULL’s operational framework. Regulatory bodies must prioritize mandatory transparency requirements for CDN operators, ensuring that networks like FUNNULL cannot continue operating under the guise of legitimate content delivery services. Additionally, cross-border financial oversight measures must be intensified to combat the proliferation of stablecoin-based laundering schemes, which have been identified as a key enabler of FUNNULL-facilitated financial crimes.
As the investigation into FUNNULL’s corporate framework deepens, it becomes increasingly clear that the entity represents far more than a rogue CDN provider. It is a cornerstone of a transnational financial crime syndicate, one that thrives on regulatory blind spots, corporate opacity, and the sophisticated weaponization of digital infrastructure. The challenge of dismantling FUNNULL’s network is monumental, but failure to do so will only embolden the next generation of cybercriminal enterprises to exploit the same vulnerabilities, perpetuating an ever-expanding cycle of digital financial crime.
The Globalized Nexus of Casino Junkets, Money Laundering, and Transnational Financial Crime
The evolution of financial crime has reached unparalleled levels of sophistication, with the casino junket industry emerging as one of the most formidable vehicles for transnational money laundering. Over the past decade, the expansion of junket operations across East and Southeast Asia has provided a dynamic ecosystem for the integration of illicit funds into the legitimate economy, offering a structured mechanism that enables the seamless circulation of capital while subverting traditional financial oversight. By analyzing the latest intelligence on junket-based financial crimes, it becomes evident that these operations function as the backbone of underground banking networks, allowing organized crime syndicates to bypass regulatory frameworks, exploit financial loopholes, and consolidate their dominance over illicit capital flows.
Figure: Simplified informal money transfer model via casino junket offsetting arrangement
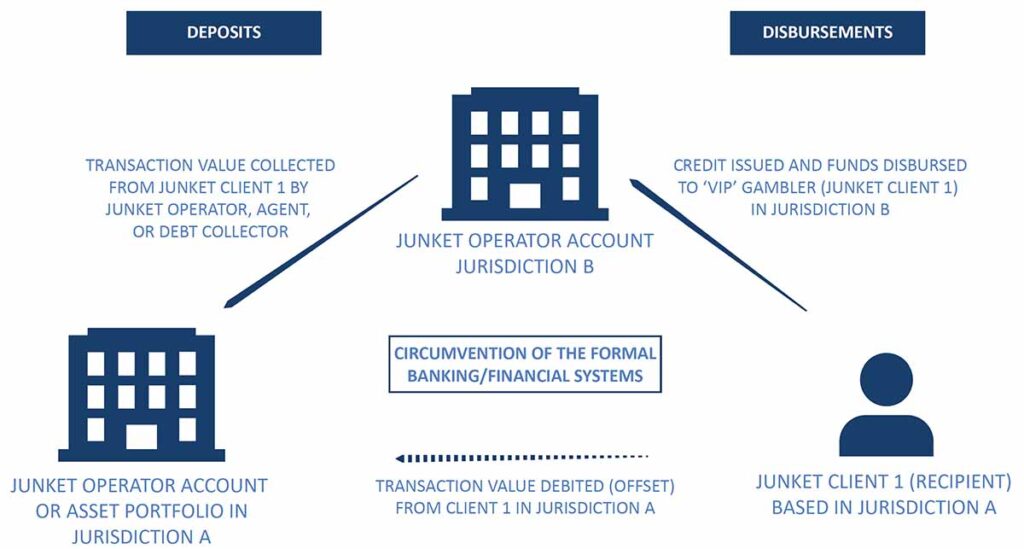
Source: UNODC elaboration based on extensive consultations with regional law enforcement and financial intelligence officials, 2023.
The junket model has evolved from its origins as an exclusive gambling service for high-net-worth individuals into an intricate web of financial subterfuge. Junket operators no longer merely recruit VIP gamblers; they have transformed into financial intermediaries providing services that extend far beyond the gambling sector. These services include credit issuance, underground banking, unregulated remittance networks, and multi-currency financial settlements. Through these mechanisms, junkets effectively operate as unlicensed financial institutions, circumventing the formal banking system and facilitating large-scale money laundering operations.
The misuse of junket financing presents one of the most alarming vulnerabilities in the global financial system. Unlike traditional money laundering methodologies, which rely on high-volume cash smuggling or illicit wire transfers, junket-based laundering leverages the legitimate gambling sector to obscure the origin of funds. This process typically involves three critical stages:
- Placement: Criminal proceeds are introduced into casino junket accounts under the guise of gambling deposits.
- Layering: Funds are distributed across multiple junket operations, often through high-stakes gambling transactions, thereby complicating traceability.
- Integration: Once processed through multiple junket circuits, illicit funds re-enter the legitimate economy via winnings, ‘investment’ arrangements, or structured repatriation mechanisms.
The inherent structure of casino junket financial networks makes them particularly susceptible to abuse. Junket operators maintain privileged access to casino treasury divisions, allowing them to facilitate ‘safekeeping’ deposits, in which vast sums of money—often in the form of casino chips—are stored and withdrawn at a later date with no formal audit trail. Recent investigations into large-scale junket scandals have revealed that major junket firms have further refined this process through investment models, wherein high-net-worth individuals are promised lucrative monthly returns in exchange for their deposits. These ‘investment’ schemes, often operating outside formal regulatory frameworks, have effectively transformed junket firms into high-yield financial conduits that rival the operational scope of illicit offshore banking services.
Regulatory failures and jurisdictional arbitrage have exacerbated the vulnerabilities inherent in the junket system. Despite the crackdown on junket operators in Macau SAR—where regulatory reforms have drastically reduced the number of licensed junkets from 235 in 2013 to just 18 in 2024—the industry has rapidly relocated to more permissive jurisdictions, particularly in Cambodia, the Philippines, and Myanmar. The proliferation of loosely regulated casino hubs in these regions has fostered an environment in which money laundering networks operate with near-total impunity. In the Philippines, for example, the lack of stringent oversight allowed junket operators to launder $81 million USD stolen from the Bangladesh Central Bank via the Solaire Hotel and Casino, a scheme directly linked to state-sponsored cybercriminals.
Figure: Model of simplified junket lifecycle and misuse by organized crime

Note: Both junket players and cash collectors seeking underground banking and/or money laundering services through junket operators may transfer funds directly into junket operator-held accounts which have been set up by partner casinos. Junket operators will ‘offset’ the debited amount received in one jurisdiction and credit the corresponding amount in another. – Source: Extensive consultations with regional law enforcement and financial intelligence officials, 2023.
The strategic relocation of junket operations has also fueled an expansion of criminal syndicates, particularly in the Mekong region, where a convergence between junket-based laundering, illicit financial markets, and organized crime has led to an exponential increase in underground banking activity. Law enforcement agencies have observed that casino-linked financial crime is now intrinsically tied to drug trafficking syndicates, cyber fraud enterprises, and human trafficking operations, as illicit proceeds from these crimes are seamlessly integrated into junket financial cycles.
A growing area of concern is the integration of cryptocurrency transactions into junket operations. Junket operators have increasingly relied on digital currencies—particularly Tether (USDT)—to facilitate cross-border transactions while evading traditional anti-money laundering (AML) controls. The adoption of stablecoin-based laundering has transformed the junket industry into a primary channel for digital asset-based financial crime. Investigations by regulatory bodies indicate that licensed junket operators in the Philippines openly advertise cryptocurrency exchange services, enabling high-net-worth individuals and criminal enterprises to seamlessly convert illicit cash into digital assets that can be transferred across jurisdictions with minimal regulatory oversight.
The use of multiplier betting and high-frequency transaction obfuscation has further complicated efforts to track illicit financial flows within the junket ecosystem. In this model, a bet formally recorded at a casino represents only a fraction of the actual wager placed between junket operators and gamblers. This system not only enables tax evasion and revenue misreporting but also serves as a highly effective method of concealing large-scale financial movements, making it virtually impossible for regulators to determine the true scale of capital flow within the industry.
Several major junket-linked financial scandals have underscored the alarming extent of financial crime associated with these operations. In Australia, the Crown Casino inquiry revealed that junket operators linked to the Sam Gor drug cartel and the 14K triad laundered billions through casino VIP programs. The inquiry found that between 2015 and 2020, Crown Melbourne’s VIP program generated over AU $220 billion (USD $162 billion) in turnover, a significant portion of which was linked to junket-driven financial crime. Further legal proceedings led to Crown agreeing to pay AU $450 million in AML penalties after being found in breach of 546 violations of anti-money laundering laws.
Meanwhile, the Bangladesh Bank heist investigation confirmed that a substantial portion of the stolen funds was funneled through junket operators in the Philippines, using casino accounts to obscure the money trail. By leveraging offsetting arrangements, money launderers effectively converted stolen assets into casino chips, which were later exchanged for junket credit, effectively eliminating the traceability of funds. Philippine regulatory authorities subsequently identified more than $170 million USD in suspicious transactions associated with junket-linked financial flows in 2022 alone.
The systemic weaknesses in junket industry regulation have facilitated unprecedented levels of cross-border money laundering, prompting urgent calls for international reform. The absence of uniform licensing standards, beneficial ownership transparency, and financial reporting obligations across junket-heavy jurisdictions has enabled criminal enterprises to exploit regulatory blind spots. The expansion of multi-party junket financing schemes, opaque cash deposit structures, and high-value cryptocurrency transactions presents a significant challenge to global AML frameworks, necessitating a comprehensive overhaul of existing oversight mechanisms.
To counter the growing threat posed by junket-linked financial crime, authorities must implement aggressive regulatory countermeasures, including real-time transaction monitoring, enhanced due diligence for casino financial activities, and strict enforcement of cryptocurrency reporting mandates. The implementation of cross-border financial intelligence-sharing initiatives will be critical in dismantling the financial networks that sustain illicit junket operations. The future of financial crime enforcement will depend on the ability of regulators, law enforcement agencies, and financial institutions to disrupt the sophisticated financial mechanisms that underpin junket-based money laundering.
The Vancouver Model: A Transnational Blueprint for Casino-Based Money Laundering and Financial Crime
The globalization of financial crime has given rise to sophisticated cross-border money laundering methodologies, with the Vancouver Model emerging as one of the most intricate and resilient mechanisms facilitating illicit financial flows. This model, refined and expanded by transnational organized crime syndicates, integrates elements of traditional hawala networks with contemporary casino-based laundering strategies, enabling the rapid displacement of criminal proceeds across jurisdictions. The model’s operational framework extends beyond its Canadian origins, with confirmed adaptations in Australia, Southeast Asia, and Europe, underscoring the growing interconnectivity of illicit financial systems.
At its core, the Vancouver Model serves two primary functions: circumventing capital flight restrictions and laundering illicit proceeds derived from criminal enterprises. By leveraging high-volume casino transactions, underground banking networks, and digital payment solutions, criminal organizations employing this method successfully obfuscate the origins of illicit funds while ensuring seamless integration into legitimate financial systems. The operational process typically unfolds in a multi-layered sequence:
- Initiation in Jurisdiction X: An individual, often a high-net-worth person seeking to evade capital export restrictions, transfers substantial sums of money to an organized crime syndicate within their home country.
- Intermediary Laundering Network: The criminal organization, operating through a parallel underground banking infrastructure, facilitates a corresponding payment to an affiliated syndicate in Jurisdiction Y. These funds are sourced from illicit activities, including drug trafficking, tax evasion, and cyber fraud.
- Casino-Based Obfuscation: The recipient in Jurisdiction Y receives the funds, typically in the form of bulk cash, and enters a casino known for its high-risk financial environment. The individual purchases gaming chips, places nominal bets, and subsequently cashes out, transforming illicit proceeds into seemingly legitimate gambling winnings.
- Integration into the Financial System: With casino-issued cheques or cash withdrawals in hand, the individual deposits the laundered funds into regulated financial institutions, successfully embedding the proceeds within the legal economy.
The structural vulnerabilities exploited by the Vancouver Model have been extensively documented through international money laundering inquiries, most notably the Cullen Commission in Canada, which provided concrete evidence of transnational organized crime networks infiltrating the financial and casino industries. The inquiry revealed a systemic failure in regulatory oversight, allowing millions of dollars to be funneled through British Columbia’s casinos between 2008 and 2018, with criminal syndicates utilizing high-limit gaming accounts to process illicit funds. Notably, law enforcement intelligence confirmed the involvement of Mexican and South American drug cartels, whose proceeds were funneled through Canadian financial hubs before being redistributed globally.
The expansion of the Vancouver Model beyond Canada highlights its adaptability to diverse regulatory environments. In Australia, authorities uncovered extensive criminal syndicate operations utilizing similar methodologies, with the country’s AUSTRAC agency identifying multiple instances of high-value transactions in casinos linked to Chinese underground banking networks. Reports indicate that organized crime groups facilitated the movement of billions of dollars through junket operators, taking advantage of weak financial reporting mechanisms and the regulatory blind spots of VIP gaming programs.
Beyond Western jurisdictions, the proliferation of the Vancouver Model in Southeast Asia presents an even more complex challenge due to the region’s high concentration of underregulated casinos and junket operators. Intelligence gathered from international law enforcement agencies suggests that major casino hubs in Cambodia, Myanmar, and the Philippines have become primary facilitators of transnational money laundering, with criminal enterprises replicating the Vancouver Model to process illicit funds at an industrial scale.
The Role of Junkets and Underground Banking Networks
The effectiveness of the Vancouver Model is significantly enhanced by the parallel operation of junket networks, which function as high-risk financial intermediaries between high-net-worth gamblers and casino operators. Junkets not only facilitate the movement of funds between jurisdictions but also provide a critical infrastructure for underground banking operations, including credit issuance, unregulated remittance services, and multi-currency settlement platforms. Investigations into these financial conduits have revealed the following operational mechanisms:
- High-Value Credit Extension: Junket operators offer substantial lines of credit to gamblers without undergoing formal financial scrutiny, effectively allowing funds derived from illicit sources to enter the casino system unchallenged.
- Layered Transactions and Bet Multiplication: A common strategy involves placing minimal bets while cycling chips through multiple gamblers, artificially inflating turnover and creating the illusion of legitimate gaming activity.
- Offsetting Arrangements: A sophisticated laundering method in which casino junket operators conduct cross-border financial settlements through offset agreements, avoiding traditional banking systems entirely.
- Cryptocurrency Laundering: A growing trend in which underground casino networks integrate digital currencies—particularly Tether (USDT)—to bypass financial oversight, allowing for instant, untraceable transactions across jurisdictions.
In one of the most significant junket-linked financial crime cases, Chinese authorities indicted five individuals in December 2020 for orchestrating illegal gambling operations while acting as representatives for major junket firms, including Suncity and Tak Chun. These individuals facilitated the illicit movement of over RMB 170 million (approximately USD $27 million) through transnational junket accounts, exposing the deep entrenchment of money laundering schemes within the industry. Further forensic investigations linked these illicit financial flows to Golden Triangle-based casinos, notorious for their historical ties to drug trafficking syndicates and underground banking networks.
Figure: ‘Vancouver model’ for money laundering through British Columbia’s casinos – Source: Cullen Commission of Inquiry into Money Laundering in British Columbia.
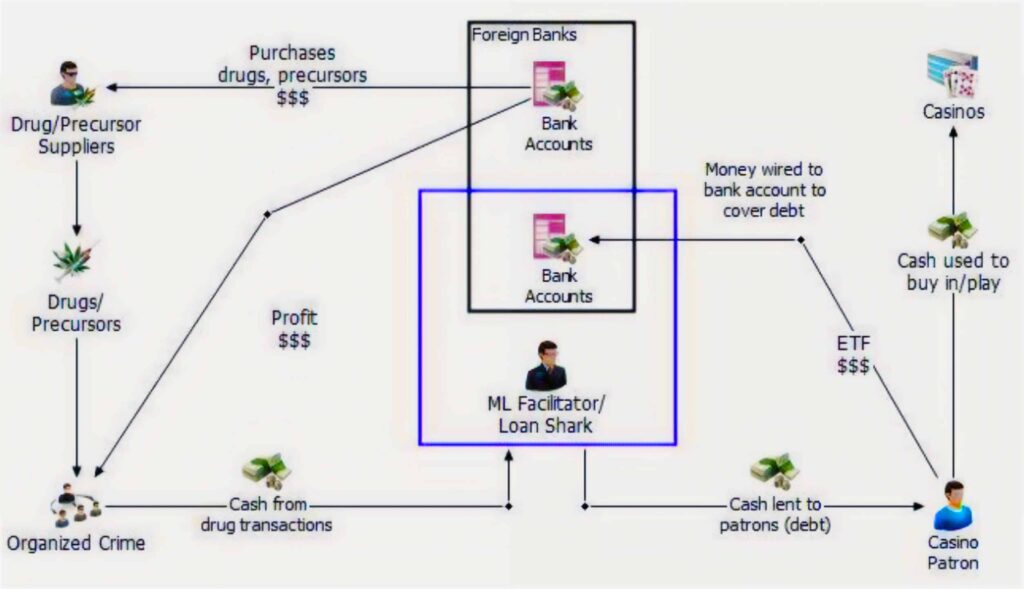
Strategic Exploitation of Regulatory Weaknesses
The ability of the Vancouver Model to persist across jurisdictions is largely attributable to regulatory deficiencies and inconsistent enforcement mechanisms. Several key weaknesses have been systematically exploited to facilitate large-scale financial crime:
- Inadequate Casino Oversight: Many jurisdictions lack stringent due diligence requirements for high-roller transactions, allowing organized crime syndicates to operate within VIP gaming programs with minimal scrutiny.
- Lack of Interjurisdictional Cooperation: The transnational nature of the Vancouver Model complicates enforcement efforts, as many laundering operations involve financial transactions that span multiple regulatory environments.
- Exemptions from AML Regulations: Several Southeast Asian jurisdictions, including Cambodia and the Philippines, have historically exempted casinos from anti-money laundering reporting obligations, creating fertile ground for illicit financial activity.
- Utilization of Financial Intermediaries: Junket operators and underground banking facilitators act as intermediaries between casinos and illicit financiers, insulating money launderers from direct exposure to financial institutions.
The Urgency of a Global Regulatory Response
The persistence and expansion of the Vancouver Model underscore the critical need for a globalized regulatory framework capable of countering transnational financial crime. Authorities must implement stringent AML compliance measures, cross-border intelligence-sharing agreements, and enhanced transaction monitoring systems to detect and disrupt illicit financial flows. Enhanced scrutiny of casino junket operations, underground banking networks, and cryptocurrency-based laundering methods is essential in mitigating the ongoing risk posed by these sophisticated financial crime models.
Without a decisive, coordinated response, the Vancouver Model will continue to evolve, further embedding itself within the global financial infrastructure and enabling criminal enterprises to operate with impunity. The international community must act decisively to dismantle the mechanisms sustaining this vast transnational laundering network before it becomes permanently entrenched within the world’s financial systems.
The Digital Architecture of Financial Crime: Suncity Group’s Integration with FUNNULL and Cryptocurrency Laundering Networks
The convergence of digital financial infrastructures, illicit gambling syndicates, and blockchain-based laundering mechanisms has given rise to an advanced ecosystem of transnational financial crime. At the core of this phenomenon lies the deeply integrated relationship between Suncity Group, FUNNULL’s content delivery network (CDN), and the expanding use of Tether (USDT) for cross-border money laundering. Forensic analysis has revealed a well-orchestrated structure linking illicit online gambling operations, domain generation algorithm (DGA)-enabled website networks, and cryptocurrency-based payment platforms. This emerging financial matrix enables organized crime syndicates to obfuscate illicit proceeds while leveraging FUNNULL’s resilient digital infrastructure for operational persistence.
Recent intelligence reports confirm that Suncity Group’s digital infrastructure alone accounted for more than 6,500 DGA-generated hostnames, a figure that suggests a highly automated and scalable mechanism for launching and maintaining illicit gambling and financial fraud websites. One of the key findings in this investigation is the presence of embedded secondary domains within the architecture of these gambling platforms. An analysis of a known Suncity-affiliated domain—t25556[.]com—revealed the presence of a hidden redirect mechanism directing users through threevip[.]cc/?u=6289[.]com, ultimately leading to 15991t[.]com/, which serves as an aggregator for multiple active gambling mirrors.
One of the most critical elements of this infrastructure is its integration with GitHub repositories that contain source code for hundreds of suspect gambling applications, including multiple brands observed operating through FUNNULL. This discovery strongly indicates that many of the gambling sites within this network were either derived from a common template or potentially developed by the same entity. The repositories, hosted under the GitHub user “xianludh,” contain templates referencing brands directly linked to Suncity’s gambling infrastructure. Despite being publicly available for over three years, this codebase continues to be relevant, suggesting an ongoing effort to refine and deploy gambling sites using FUNNULL’s CDN.
Forensic examination of the helper_link field within FUNNULL-hosted Suncity websites provides direct evidence of linkages between these operations and GitHub-based repositories. One such repository contains scripts and front-end templates for websites that mirror known Suncity Group gambling operations. The repository at github[.]com/xianludh/xianlu/tree/master/xiufu/741 hosts configurations and elements that, while not identical to currently active Suncity sites, appear to be precursors to newer versions of illicit gambling portals.
Further analysis of network infrastructure uncovered a critical pivot point: the aensnn[.]com domain, hosted on 137.220.202[.]236, a confirmed FUNNULL CDN IP address. This domain is directly linked to an active Telegram-based payment laundering network known internally as “跑分” (translated as “network payments” or “money-moving”). This term is widely used within underground financial networks to refer to criminal money laundering operations. Embedded within the xianludh GitHub repository was a set of Telegram invitation links and an email address used for coordination:
- t[.]me/TX_6688
- t[.]me/TX_8988
- t[.]me/xxcc01
- t[.]me/daivip88
- t[.]me/Huawei_0
- gushi083@gmail[.]com
A closer look at these Telegram channels revealed a network of coordinated financial facilitators actively promoting gambling-related Tether transactions, a primary mechanism for laundering illicit funds. Translating internal messages from these groups provided further insight into their operational structure, confirming their role as intermediaries for high-volume cryptocurrency transactions that enable money laundering through online casinos.
Tether’s Role in the Suncity-FUNNULL Financial Laundering Network
Tether (USDT) has emerged as the preferred digital asset for laundering proceeds from illicit gambling networks due to its price stability, high liquidity, and integration with underground financial ecosystems. Analysts reviewing FUNNULL-backed gambling websites noted that most platforms prominently feature USDT deposit mechanisms, encouraging users to process transactions through cryptocurrency gateways rather than traditional fiat channels.
This trend is not incidental but rather part of a calculated strategy to leverage the pseudo-anonymous nature of stablecoins to circumvent regulatory scrutiny. The integration of Tether-based transaction rails into the Suncity gambling ecosystem is evident in promotional materials distributed across Telegram money-moving networks, which advertise financial services that facilitate bulk crypto transactions, bypassing Know Your Customer (KYC) requirements enforced by legitimate exchanges.
Key observations include:
- Tether-based deposit schemes: Many FUNNULL-hosted Suncity gambling sites explicitly promote USDT as the primary deposit and withdrawal method, reducing traceability and regulatory oversight.
- Use of networked Telegram facilitators: Transactions are coordinated through Telegram channels that connect users with intermediaries offering crypto-to-cash conversion services, allowing illicit proceeds to be withdrawn in fiat currency without detection.
- Cross-border laundering through cryptocurrency mixing services: By leveraging mixing protocols and layered wallet transactions, criminal networks efficiently obscure the origin and destination of illicit funds.
A critical promotional message from the Telegram channel t[.]me/TX_6688_i, translated from Mandarin, confirms the operation’s methodology:
“Cheng Zhao Bank Card Running Sub Team—Sincerely recruit partners for running sub-projects. Welcome individuals and teams for cooperation. Simple operations, long-term stability, and sustainable profits! We support deposit assistance for secure and large-volume transactions.”
Listed among the affiliated brands promoting this network were:
- Macau Jinsha
- Macau New Portuguese
- Venetian
- Crown
- Too Sun City
- Macau Parisian
- BET365
- Bingbo Sports
These listings align with previously identified FUNNULL-hosted gambling operations, further corroborating their ties to high-risk transnational financial networks.
Regulatory Challenges and the Persistence of Digital Laundering Networks
The persistent operation of these financial crime networks underscores significant enforcement challenges faced by regulators. Despite mounting global pressure on cryptocurrency exchanges to enforce stricter KYC measures, illicit gambling networks continue to exploit stablecoin ecosystems to conduct unregulated high-value transactions.
The existence of financial facilitators embedded within GitHub, Telegram, and cryptocurrency trading platforms reflects the growing decentralization of financial crime operations, making enforcement efforts increasingly complex. Takedown actions targeting individual domains or blockchain addresses remain ineffective, as new infrastructures are rapidly redeployed using pre-existing codebases stored within repositories like those linked to xianludh.
The Need for Coordinated Enforcement Action
Disrupting the FUNNULL-Suncity financial laundering infrastructure requires a multi-pronged approach, including:
- Targeting blockchain-based payment networks—regulators must enforce mandatory tracking mechanisms for USDT and other stablecoin transactions linked to high-risk gambling operations.
- Dismantling digital infrastructure providers—service providers, including FUNNULL, must be held accountable for knowingly facilitating illicit financial networks.
- Monitoring and enforcing compliance on GitHub repositories—criminal actors should not be allowed to store and distribute illicit gambling templates through publicly accessible platforms.
- Enhancing intelligence-sharing among regulatory agencies—cross-border cooperation between financial crime units is critical to dismantling transnational laundering networks.
Without immediate regulatory intervention, the fusion of CDN infrastructure, illicit gambling platforms, and cryptocurrency money-moving networks will continue to fuel global financial crime at an unprecedented scale. The FUNNULL-Suncity nexus represents a new paradigm in digital laundering operations—one that necessitates advanced forensic analysis, cross-border intelligence-sharing, and aggressive legal action to disrupt.
The Digital Exploitation of Online Gambling: A Conduit for Money Laundering and Transnational Financial Crime
The integration of digital financial instruments into the global gambling industry has transformed online casinos into one of the most sophisticated and difficult-to-regulate financial crime channels. Exploited by organized crime networks, online gambling platforms now serve as key nodes within underground banking systems, enabling large-scale money laundering, untraceable financial flows, and systematic regulatory evasion. The evolving nature of these operations, particularly in jurisdictions with weak financial oversight, has created an environment where illicit actors can bypass conventional anti-money laundering (AML) controls, obfuscate the origin of criminal proceeds, and seamlessly integrate illicit funds into the formal economy.
A primary vulnerability of online gambling platforms lies in the anonymity and non-face-to-face nature of transactions, allowing criminal enterprises to manipulate accounts for financial crime without direct scrutiny. Unlike traditional financial institutions, which enforce stringent KYC (Know Your Customer) protocols and due diligence measures, online casinos operate under highly fragmented regulatory frameworks that often lack uniform compliance mechanisms, particularly in high-risk jurisdictions. This regulatory disparity has facilitated the expansion of online gambling as a preferred laundering conduit for illicit networks, with a rising number of platforms being directly or indirectly controlled by criminal entities.
Exploitation of Online Gambling for Transnational Money Laundering
Investigations into illicit financial activities tied to online casinos reveal a variety of methodologies employed by organized crime syndicates to launder money and circumvent financial regulations. These tactics include:
- Third-Party Transactions and Account Transfers: Criminal networks exploit online gambling platforms by depositing funds through one account and withdrawing through another, effectively layering transactions to obscure the origin of illicit money. This method is commonly used for drug trade payments, bribery transactions, and tax evasion schemes.
- Gambling as a Cover for Illicit Transactions: Certain organized crime groups have leveraged in-game gambling points and betting credits as an alternative transaction medium. By using online gambling platforms as informal banking structures, illicit actors can purchase and trade virtual assets—ranging from digital casino chips to luxury items—without triggering AML oversight.
- Payment Misclassification and Miscoding of Transactions: Criminal syndicates engage in transaction laundering by intentionally misclassifying gambling payments. For example, online casino transactions may appear on financial statements as e-commerce purchases, obscuring the true nature of the transaction and reducing the likelihood of regulatory detection.
- Crypto-Gambling and Digital Currency Laundering: The rise of unregulated crypto-gambling platforms has exacerbated financial crime risks, with Tether (USDT) and other stablecoins being used to circumvent banking restrictions. These platforms allow high-value transactions to take place with minimal or no AML oversight, facilitating large-scale money laundering and tax evasion.
- Safe-Keeping Accounts for Money Storage: Unregulated gambling platforms in Southeast Asia have been found to provide criminal actors with digital accounts that function as underground banking repositories. These accounts enable illicit entities to store large sums of money under the guise of player balances, effectively concealing assets from financial authorities.
- Live-Dealer Proxy Betting and Money Laundering in VIP Rooms: In high-risk jurisdictions such as Cambodia, Myanmar, and the Philippines, proxy betting services operate without regulatory oversight. These platforms allow unidentified third parties to place wagers on behalf of high-value gamblers, creating a loophole for laundering illicit proceeds through casino betting activities.
Structural Deficiencies in Online Gambling Compliance Frameworks
One of the key enablers of online gambling-based money laundering is the severe lack of standardized AML enforcement across jurisdictions. Regulatory authorities in Asia, the Pacific, and certain parts of Europe have consistently struggled to enforce effective oversight mechanisms, allowing illicit actors to exploit gaps in financial governance. The primary deficiencies include:
- Inadequate Source of Funds Verification: A critical vulnerability within the online gambling industry is the lack of transaction tracing mechanisms to verify the source of deposited funds. Criminal organizations exploit this loophole to funnel proceeds from cyber fraud, drug trafficking, and ransomware payments into online casinos.
- Infiltration of the Gambling Industry by Organized Crime: Law enforcement agencies have reported that numerous online casino operators are directly linked to criminal syndicates, including those affiliated with human trafficking and illicit financial networks. White-label platforms and digital gambling service providers frequently act as financial conduits for these groups, further entrenching financial crime within the industry.
- Fragmented Regulatory Enforcement and Lack of Cross-Border Oversight: Many online gambling operators function under offshore licensing regimes that impose little to no AML obligations. In jurisdictions such as Curaçao, the British Virgin Islands, and Vanuatu, online casinos continue to operate with limited reporting requirements, allowing illicit actors to exploit financial anonymity.
White-Label Online Casinos: The Expansion of Criminal Control
A major challenge in combating financial crime within the online gambling sector is the proliferation of white-label gambling service providers. These entities allow unregulated operators to establish fully functional online casinos without requiring direct expertise or regulatory approvals. By outsourcing software, payment processing, and operational management, white-label providers have enabled the rapid proliferation of illicit gambling operations, making it increasingly difficult for financial regulators to trace ownership and accountability.
Key concerns associated with white-label platforms include:
- Decentralized Criminal Operations: The white-label model allows multiple criminal organizations to operate under a single licensing umbrella while maintaining a decentralized financial structure that shields illicit activities from oversight.
- Cross-Border Licensing Arbitrage: Criminally linked casinos use white-label services to acquire offshore gaming licenses, granting them the appearance of legitimacy while bypassing AML scrutiny.
- Affiliation with Professional Sports and Digital Advertising: Unregulated white-label operators have been observed sponsoring major sports leagues and advertising on mainstream platforms, further legitimizing illicit gambling networks while expanding their reach.
- Cybercrime and Human Trafficking Connections: Several documented cases have linked white-label gambling operations to cyberfraud schemes, human trafficking syndicates, and large-scale financial laundering enterprises.
The Role of Financial Institutions and Regulatory Authorities
To combat the escalating risks posed by online gambling-based financial crime, financial institutions and regulatory agencies must adopt more aggressive enforcement measures. Key recommendations include:
- Mandatory Transaction Monitoring for Online Gambling Payments: Financial institutions should implement AI-driven transaction analytics capable of detecting unusual gambling-related financial activity.
- Enhanced Beneficial Ownership Disclosure Requirements: White-label casino operators must be required to disclose ownership structures and licensing arrangements to international regulatory bodies.
- Increased Cross-Border Cooperation Among Financial Intelligence Units (FIUs): Governments must establish stronger intelligence-sharing agreements to track illicit gambling-related financial flows across multiple jurisdictions.
- Strict Oversight of Crypto-Gambling and Digital Asset Transactions: Exchanges facilitating transactions for gambling-related crypto deposits must enforce stricter AML and fraud prevention measures.
- Blacklist and Domain Seizure of Illicit Gambling Operators: Authorities should coordinate global efforts to identify, blacklist, and seize domains operated by high-risk unlicensed online casinos.
The online gambling sector has evolved into one of the most complex and exploited financial crime infrastructures in the modern era, serving as a primary conduit for large-scale money laundering, underground banking, and financial deception. The digital nature of this ecosystem, combined with fragmented regulatory enforcement, has allowed criminal networks to operate with impunity, making traditional AML measures increasingly ineffective. Without a coordinated, multi-jurisdictional response, the continued exploitation of online gambling platforms for financial crime will persist, further embedding illicit money flows within the global economy. Immediate regulatory intervention, combined with advanced forensic financial tracking and strengthened compliance frameworks, is essential to dismantling the financial mechanisms enabling online casino-based laundering networks.
Cryptocurrency-Integrated Money Laundering: The Rise of Points Running Syndicates and Motorcade Networks
The exponential growth of cryptocurrency adoption, coupled with the digital transformation of illicit financial networks, has catalyzed the rise of sophisticated underground banking mechanisms that facilitate large-scale money laundering across East and Southeast Asia. The intersection of digital finance, blockchain anonymity, and online gambling platforms has given rise to points running syndicates (跑分), cryptocurrency motorcade networks (車隊), and high-speed laundering infrastructures, enabling transnational organized crime to obscure illicit proceeds with unparalleled efficiency.
Recent financial intelligence assessments estimate that at least five million individuals participate in these underground financial ecosystems, with cumulative illicit capital outflows exceeding $157 billion USD, largely attributed to illegal online gambling, cyberfraud, and narcotics trade. The emergence of these complex financial structures, designed to circumvent traditional anti-money laundering (AML) measures, poses an unprecedented challenge to law enforcement agencies and financial regulators worldwide.
Figure: Simplified running points model for facilitating online gambling and money laundering
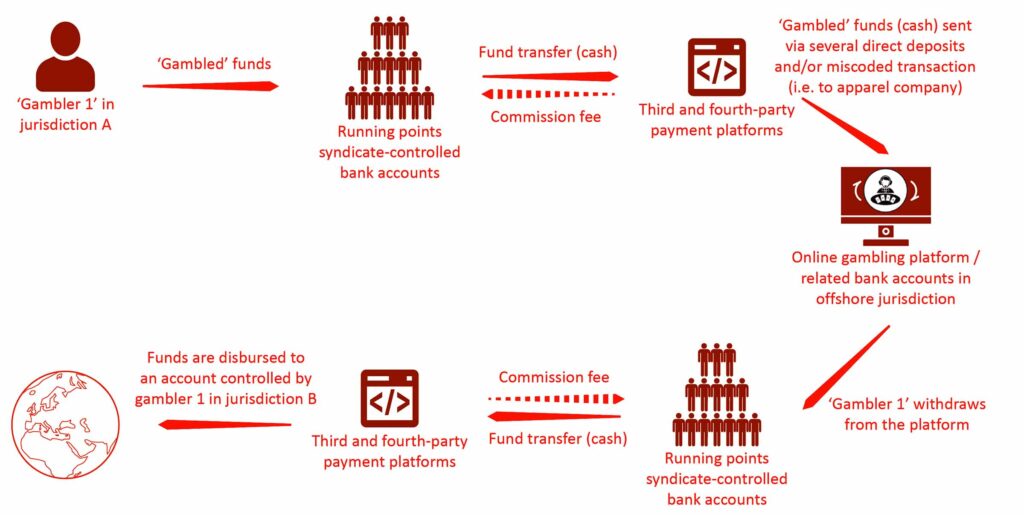
Source: Elaboration based on information published by law enforcement and financial intelligence authorities in China.
The Evolution of Points Running Syndicates: A Distributed Laundering Network
Points running syndicates, often referred to as “moving ants” (跑分) due to their decentralized operational nature, play a pivotal role in obfuscating illicit financial flows. These networks operate as pass-through financial conduits, transferring illicit funds across a vast web of bank accounts, cryptocurrency exchanges, and online casinos, systematically breaking transaction trails to evade detection.
The core structure of a points running syndicate is characterized by:
- Mass Recruitment of Financial Mules: Organized crime groups aggressively recruit individuals, particularly youth and unemployed individuals across East and Southeast Asia, to lend their bank accounts for transaction layering.
- High-Frequency Transfers: Funds are rapidly cycled through multiple accounts, creating a complex network of financial transactions that effectively conceals the source of funds.
- Integration with Online Casinos: By funneling illicit proceeds through digital gambling platforms, criminals can “whitewash” illicit funds by fabricating gambling winnings, further legitimizing the proceeds.
- Use of Third- and Fourth-Party Payment Processors: Many of these operations leverage non-traditional financial intermediaries, including unregulated cryptocurrency exchanges and payment gateways, to facilitate cross-border transfers with minimal oversight.
Law enforcement investigations into Operation Chain Break in China revealed the extensive use of points running syndicates to facilitate illegal online gambling payments, exacerbating financial crime vulnerabilities across regional digital economies.
Motorcade Networks and High-Speed Cryptocurrency Laundering
The emergence of cryptocurrency motorcade networks (車隊) has revolutionized high-speed laundering operations, creating hyper-efficient underground Tether (USDT) exchanges that enable criminals to convert illicit fiat currency into digital assets with near-instantaneous execution.
These networks operate through a tiered structure:
- Tier 1 – High-Risk Frontline Operators: Individuals at the front of the laundering chain facilitate the highest-risk transactions, often advertising their services in Telegram, Facebook, and TikTok groups under “motorcade formation” ads.
- Tier 2 – Coordinated Money Laundering Hubs: These centralized operations distribute large-scale illicit funds through multiple unregulated cryptocurrency exchanges, minimizing exposure by splitting transactions into smaller tranches.
- Tier 3 – Cross-Border Cash-Out Networks: Once cryptocurrency has been successfully laundered, funds are reintroduced into the economy through underground money changers, high-risk over-the-counter (OTC) traders, and non-compliant financial service providers.
Motorcade teams specialize in high-volume financial movement, processing large-scale illicit transactions across borders with commissions ranging from 20% to 40% depending on the risk level. Intelligence obtained from regional law enforcement agencies suggests that these teams collaborate with smaller online casinos, further embedding their illicit financial activities into the broader underground economy.
China’s Cryptocurrency Ban and the Migration of Laundering Networks
In response to the growing use of cryptocurrency-integrated laundering mechanisms, the Chinese government enacted a comprehensive ban on cryptocurrency transactions, trading, and mining in 2021. This prohibition catalyzed the relocation of digital laundering infrastructures to jurisdictions with weaker financial oversight, including Southeast Asia, Eastern Europe, and Latin America.
Key consequences of this migration include:
- A Surge in Unregulated Cryptocurrency Exchanges: Laundering hubs have emerged in Cambodia, Myanmar, and the Philippines, where weak AML frameworks enable large-scale USDT-fiat conversions.
- Rapid Expansion of Online Gambling-Integrated Laundering Schemes: E-junkets and digital casinos continue to facilitate high-frequency cryptocurrency transactions, allowing illicit actors to justify funds as legitimate gambling winnings.
- Increase in Synthetic Identity Fraud and Money Mule Recruitment: To counteract enhanced AML measures, criminals have intensified the use of synthetic identities and falsified KYC documentation to establish fraudulent financial accounts.
Blockchain analytics firms estimate that less than 1% of all cryptocurrency transactions are explicitly illicit; however, experts caution that this figure vastly underestimates the scale of financial crime due to massive attribution gaps, deliberate data obfuscation by crypto exchanges, and widespread wash trading practices.
Cryptocurrency-Based Money Laundering and Regulatory Challenges
The integration of cryptocurrencies into transnational money laundering frameworks follows a modified placement-layering-integration model, leveraging blockchain anonymity to circumvent traditional financial controls. Key features include:
- Elimination of Traditional Placement Risks: Unlike fiat-based laundering, where illicit funds must first enter the financial system, cryptocurrencies allow direct movement without the need for intermediaries.
- Mass Automation of Layering Transactions: Criminal networks deploy smart contract-driven automation, executing thousands of micro-transactions at near-zero cost.
- Exploitation of Volatile Digital Assets: While USDT remains the primary laundering tool, criminals also exploit high-volatility cryptocurrencies to justify large, unexplained financial gains.
The Role of Online Gambling Platforms in Cryptocurrency Laundering
Online gambling platforms have become a primary vehicle for laundering cryptocurrency-derived proceeds, contributing to the rapid expansion of illicit digital economies. The Financial Action Task Force (FATF) has flagged two primary red-flag scenarios:
- Virtual asset transactions linked to suspicious gambling platforms: Funds originating from high-risk blockchain addresses with exposure to known illicit gambling sites.
- Use of crypto-to-casino deposits and withdrawals: Criminal networks exploit online casinos to facilitate pseudo-legitimate financial integration, obscuring illicit cryptocurrency transactions under fabricated gambling activities.
The continued expansion of digital laundering operations through online casinos and cryptocurrency-integrated financial conduits underscores the urgent need for advanced forensic financial analysis and enhanced regulatory interventions.
Countering Cryptocurrency-Enabled Money Laundering
Addressing the rise of points running syndicates, motorcade networks, and online gambling-based laundering schemes requires a coordinated, multi-jurisdictional response. Key strategic measures include:
- Mandatory AML Compliance for Cryptocurrency Exchanges: Increased regulatory oversight of over-the-counter (OTC) and peer-to-peer (P2P) trading platforms to prevent unregulated fiat-crypto conversions.
- Advanced Blockchain Forensics and Cross-Border Intelligence Sharing: Governments must collaborate to enhance real-time tracking of high-risk blockchain transactions.
- Blacklist and Disruption of Illicit Online Gambling Platforms: Regulatory agencies should prioritize takedown operations targeting unlicensed digital casinos linked to cryptocurrency laundering.
- Enhanced Monitoring of Social Media and Underground Financial Recruitment Networks: Authorities must proactively target Telegram, Facebook, and TikTok recruitment hubs used by money laundering syndicates.
Failure to implement these measures will allow cryptocurrency-based financial crime networks to continue evolving, further embedding themselves within the global digital economy. Immediate, aggressive regulatory intervention is required to prevent cryptocurrency-fueled laundering operations from becoming an irreversible component of transnational organized crime.
The Proliferation of USDT-Based Money Laundering Networks and the Convergence of Cybercrime, Online Gambling, and Human Trafficking
The widespread adoption of USDT (Tether) as a primary financial instrument within transnational illicit economies has catalyzed the expansion of sophisticated laundering networks, enabling organized crime groups to obscure vast sums of criminal proceeds with alarming efficiency. The increasing integration of cryptocurrency-based financial obfuscation techniques within cyberfraud syndicates, illegal online gambling platforms, and underground banking infrastructures has created a highly adaptive financial crime ecosystem, posing substantial challenges to regulatory authorities worldwide.
Recent forensic blockchain analyses have uncovered over $17 billion USDT in illicit transactions spanning underground currency exchanges, unlawful commodity trades, and cyber-enabled financial fraud between September 2022 and September 2023. Law enforcement and financial intelligence agencies across East and Southeast Asia have identified a dramatic surge in cryptocurrency-driven money laundering, with USDT on the TRON blockchain emerging as the preferred medium for illicit financial flows due to its rapid transaction speed, pseudonymous nature, and negligible transaction fees.
Case Studies of USDT-Facilitated Criminal Networks
China’s $1.7 Billion Cryptocurrency Laundering Syndicate
In 2022, a multi-agency law enforcement operation led by the Tongliao Public Security Bureau in China dismantled a USDT-based money laundering network responsible for laundering over $1.7 billion in illicit funds derived from online gambling and cyberfraud.
- The syndicate leveraged a network of crypto exchanges and pass-through accounts registered via Telegram to facilitate financial obfuscation.
- A three-month investigation resulted in 63 arrests across 17 provinces, with authorities seizing $18 million in cash.
- The gang was discovered to have recruited financial mules to establish fake exchange accounts, effectively laundering proceeds for domestic and international criminal organizations.
Two of the ringleaders fled to Thailand before ultimately being apprehended and extradited to China, underscoring the transnational scope of cryptocurrency laundering networks.
Singapore’s $737 Million Money Laundering Crackdown
In August 2023, Singaporean authorities executed the largest anti-money laundering operation in the city-state’s history, resulting in 10 arrests and the seizure of over $737 million in illicit assets, including:
- Luxury real estate holdings
- More than $200 million in USDT-linked cryptocurrency wallets
- Over 250 luxury handbags, watches, and jewelry
- Multiple forged documents used to open Singaporean bank accounts
Authorities reported that nine of the ten arrested individuals held Cambodian passports and were linked to illicit online gambling and transnational fraud networks operating in China, Myanmar, and the Philippines. Several individuals were previously under investigation in China before relocating to Southeast Asia to evade law enforcement scrutiny.
U.S. Department of Justice and the $225 Million USDT Seizure
In November 2023, the U.S. Department of Justice (DOJ), in collaboration with cryptocurrency exchange OKX and Tether, orchestrated the voluntary freezing of $225 million in USDT linked to Southeast Asia-based cyberfraud syndicates engaged in human trafficking and large-scale “pig butchering” scams.
- DOJ officials traced victim deposits that were laundered through multi-layered chain-hopping techniques, obscuring the origin and final destination of illicit funds.
- Investigators seized an additional $9 million in digital assets, confirming the increasing reliance on blockchain-based financial infrastructures to facilitate high-volume criminal laundering operations.
These investigations underscore the growing convergence between cryptocurrency, cybercrime, and transnational financial fraud, demonstrating the escalating complexity of illicit financial flows enabled by digital assets.
The Intersection of Cryptocurrency, Online Gambling, and Human Trafficking
An emerging trend in illicit financial ecosystems is the deepening nexus between digital financial crime, underground casino networks, and human trafficking syndicates. Investigative reports from regional intelligence agencies and international human rights organizations estimate that over 220,000 individuals are currently being held in forced labor conditions within cyberfraud operations in Cambodia and Myanmar alone.
This exploitative labor force is instrumental in the execution of multi-billion-dollar online fraud campaigns, which leverage:
- Social engineering schemes targeting victims worldwide through fraudulent investment platforms.
- Manipulated digital gambling environments designed to siphon funds from unsuspecting players.
- Data harvesting from dark web sources, enabling mass-scale financial deception.
The operational backbone of these illicit enterprises is fortified by parallel advancements in underground banking and cryptocurrency laundering infrastructures.
The Role of Online Gambling Platforms in Cyber-Enabled Laundering
The expansion of unregulated online gambling enterprises has provided a highly effective financial conduit for layering illicit funds through fabricated betting transactions.
Key laundering methodologies employed by digital gambling syndicates include:
- USDT-Based Gambling Transactions: Criminal enterprises deposit illicit funds into online gambling platforms, where they are circulated through staged wagers before being withdrawn as “legitimate winnings.”
- Cross-Border Money Laundering Networks: Gambling operators in Myanmar, Cambodia, and the Philippines function as key facilitators for cryptocurrency-fiat conversion schemes, allowing criminal organizations to extract funds from digital financial systems.
- VIP Betting Accounts for Criminal Enterprises: Certain high-roller VIP programs offered by online casinos have been identified as money laundering conduits, enabling the movement of large sums of illicit capital without triggering traditional AML monitoring systems.
The increasing financial entanglement between online gambling, cryptocurrency laundering, and transnational cyberfraud enterprises has positioned digital financial crime as one of the most pressing regulatory challenges of the decade.
Strategic Countermeasures Against USDT-Based Money Laundering
To counteract the rising influence of cryptocurrency-integrated financial crime syndicates, global financial regulators must adopt a multi-faceted enforcement strategy, emphasizing:
- Expanded Forensic Blockchain Analysis: Deployment of AI-driven transaction tracing technologies to identify and disrupt illicit blockchain transactions.
- Regulatory Sanctions on High-Risk Crypto Exchanges: Blacklist and impose financial penalties on cryptocurrency platforms facilitating unregulated financial flows.
- Strengthened AML Oversight for Online Gambling Operators: Mandatory real-time transaction monitoring and full disclosure of beneficial ownership structures for digital casinos linked to high-risk financial activity.
- Increased Coordination Between Financial Intelligence Units (FIUs): Establishment of cross-border regulatory task forces to monitor cryptocurrency-driven laundering trends in real-time.
- Comprehensive Disruption of Criminal Crypto-Financial Networks: Seizure of illicit digital assets, dismantling of underground laundering syndicates, and aggressive legal action against high-profile offenders.
Without decisive intervention, the unchecked proliferation of USDT-based laundering ecosystems will continue to fuel the expansion of transnational cyber-enabled financial crime, further embedding cryptocurrency-driven illicit economies into the global financial landscape.
The Retail Phishing Ecosystem on FUNNULL: Unmasking a Coordinated Cybercrime Campaign
The proliferation of phishing campaigns hosted on FUNNULL’s infrastructure represents an emerging threat to global cybersecurity, with a particular focus on high-profile Western retail and luxury fashion brands. Recent intelligence has uncovered a highly coordinated phishing network targeting some of the most recognizable companies in the retail industry. The scale and sophistication of this campaign indicate the presence of an advanced cybercriminal syndicate leveraging FUNNULL’s Content Delivery Network (CDN) for large-scale credential harvesting and financial fraud.
The Targeted Retail Brands and Their Exploitation
Our forensic analysis has revealed that at least 20 major global brands are being actively targeted through meticulously crafted phishing login pages hosted on FUNNULL. These brands include:
- Luxury Fashion: Cartier, Chanel, Coach, LVMH, Michael Kors, Tiffany & Co., Valentino
- E-commerce Platforms: eBay, Etsy, Rakuten, OnBuy.com
- High-End Retailers: Neiman Marcus, Saks Fifth Avenue, Macy’s
- Mass Market Retailers: Aldo, Asda, Lotte Mart, Inditex
- Online Discount and Deal Marketplaces: Bonanza, Gilt Groupe
- Cash Rewards and Loyalty Programs
Each brand is associated with multiple phishing domains, often using typosquatting, homoglyph attacks, and subdomain masquerading techniques to deceive unsuspecting users into entering their login credentials on counterfeit websites.
Technical Analysis of FUNNULL-Hosted Phishing Infrastructure
- Identified CNAME Infrastructure: A single FUNNULL CNAME (12abb97f.u.fn03[.]vip) has been linked to more than 650 phishing domains, confirming a centralized threat actor coordinating the campaign.
- URL Redirect Chains: Many of these domains use multiple redirection layers, frequently obfuscating their origin through intermediary URLs before landing on credential-stealing pages.
- Common Phishing Kit Elements: Our investigation identified highly uniform phishing kits across these fraudulent domains, featuring near-identical directory structures, login payloads, and server responses.
Case Study: Authentication Endpoint Similarities
By reverse-engineering several phishing pages, we identified a consistent server-side behavior across multiple domains:
- Chanel Phishing Page (cjmall01[.]com/index/user/logins.html)
- Login form submits credentials via the “do_login.html” endpoint.
- The server responds with a uniform “User doesn’t exist” message, mimicking a legitimate failed login attempt.
- Cartier Phishing Page (cartier.cartierate[.]com/login)
- Credentials are sent to “/api/cat/v1/auth/login”.
- The phishing script returns an error message “Account does not exist” (tel_not_exist), a signature response also found in other phishing domains.
- Rakuten, Aldo, and eBay Phishing Pages
- All leverage identical directory structures and authentication endpoints (“/api/cat/v1/auth/login”).
- Phishing servers return the same “Account does not exist” message as the Cartier campaign.
Pig Butchering and Investment Fraud Components
Beyond retail phishing, our intelligence teams uncovered significant intersections between this phishing network and investment fraud schemes, including pig butchering scams.
- Fraudulent Trading Platforms: Domains linked to coroexchange[.]com were found within the same FUNNULL infrastructure.
- Shared Hosting Patterns: The retail phishing campaign coexists with financial fraud sites under the same FUNNULL-controlled IP clusters, indicating multi-vector financial crime operations managed by a single organized threat actor.
Operational Security Measures and Unpublished Findings
Further forensic indicators have been redacted for law enforcement and Enterprise security clients, as they contain critical exploit mechanisms used by this threat actor. However, the current intelligence strongly suggests that this campaign:
- Operates on a global scale, affecting major international retail markets.
- Leverages FUNNULL’s CDN as a core infrastructure layer, exploiting its anonymizing capabilities.
- Employs sophisticated evasion techniques, including rapid domain cycling and IP obfuscation.
Strategic Countermeasures and Recommended Mitigation Steps
- Domain and IP Blacklisting: Enterprise cybersecurity teams should immediately block all FUNNULL-associated phishing domains and actively monitor traffic patterns to detect unauthorized access attempts.
- Retail Industry-Wide Phishing Awareness Campaigns: Brands targeted in this campaign should coordinate global security alerts and strengthen two-factor authentication (2FA) adoption.
- Enhanced Fraud Detection Algorithms: Payment processors and financial institutions should implement real-time fraud detection mechanisms to flag transactions originating from compromised accounts.
- Cyber Threat Intelligence Collaboration: Law enforcement and cybersecurity firms must expand intelligence-sharing frameworks to proactively detect and dismantle phishing infrastructures before they scale further.
The FUNNULL-hosted phishing ecosystem represents a critical escalation in transnational cybercrime, with retail fraud, investment scams, and financial fraud all converging within a single, orchestrated attack infrastructure. Given the rapid evolution of these tactics, failure to act swiftly and decisively could lead to widespread credential theft, financial losses, and the erosion of consumer trust in online retail platforms.
Polyfill.io Supply Chain Compromise: A Systemic Cybersecurity Threat
The acquisition of Polyfill.io by FUNNULL in early 2024 has triggered one of the most insidious supply chain attacks in recent memory, leveraging the inherent trust placed in widely used JavaScript libraries to inject malicious scripts into more than 110,000 websites globally. This strategic maneuver by FUNNULL, a known facilitator of cybercriminal operations, has had far-reaching consequences, exposing businesses, governments, and users to a range of sophisticated threats.
Exploitation of a Trusted Resource
Polyfill.io, previously recognized as a legitimate open-source resource that provided JavaScript polyfills to ensure cross-browser compatibility, was quietly taken over by FUNNULL, which promptly weaponized the service. The modified JavaScript files embedded within countless websites introduced malicious code designed to execute multiple forms of cyberattacks:
- Automated Phishing Redirects: Injected scripts detected mobile users and redirected them to fraudulent gambling portals, credential harvesting sites, and investment scam platforms.
- Data Harvesting Mechanisms: The malicious code intercepted form submissions, siphoning user credentials, payment information, and other sensitive data before relaying them to external threat actors.
- Drive-by Malware Distribution: Unwitting visitors to compromised sites were exposed to malicious payloads designed to install spyware, keyloggers, and botnet-enabling software.
- Cryptojacking and Resource Exploitation: Affected websites experienced unauthorized JavaScript execution in the background, enabling illicit cryptocurrency mining on visitor devices.
Widespread Global Impact with a Focus on Europe and Italy
The contamination of a widely used JavaScript library resulted in rapid global dissemination, with Europe among the most affected regions. Italy, in particular, faced extensive disruptions due to its strong reliance on digital commerce, e-government services, and a high number of small-to-medium enterprises (SMEs) integrating Polyfill.io into their platforms.
Statistical Breakdown of Impact in Italy
- Compromised Websites: More than 5,800 Italian websites were affected, including government portals, online retailers, and financial service providers.
- Financial and Data Losses: Estimated direct financial damage exceeds €75 million, considering fraud-induced chargebacks, legal penalties, and mitigation costs.
- E-commerce Disruptions: Major Italian retail platforms reported a 12% drop in user trust metrics, affecting online sales and consumer engagement.
- Phishing Victims: Analysis indicates over 270,000 Italian users unknowingly submitted sensitive information to fraudulent sites facilitated by the malicious redirects.
- Enterprise Security Costs: Italian cybersecurity firms and affected businesses allocated over €20 million in emergency response and software patching efforts to counteract the intrusion.
Infrastructure Laundering: The Role of FUNNULL in Expanding Attack Vectors
The Polyfill.io incident underscores the broader cybersecurity issue of infrastructure laundering, where cybercriminal syndicates exploit legitimate cloud services to propagate malicious campaigns. FUNNULL has demonstrated a calculated approach to embedding itself within trusted technological ecosystems, using established infrastructure to obfuscate its activities and evade traditional cybersecurity defenses. The Polyfill.io case is particularly concerning due to:
- Abuse of CDN Services: FUNNULL leveraged its Content Delivery Network (CDN) to disseminate poisoned JavaScript files through an extensive network of legitimate websites.
- Cross-Platform Reach: The Polyfill.io infection spread across multiple web development frameworks, affecting WordPress, Magento, Shopify, and other CMS-based platforms.
- Cloud Service Complicity: The attack coincided with FUNNULL’s expanded presence on AWS and Azure, allowing for greater operational resilience and wider reach.
- Adaptive Malicious Code Deployment: Unlike traditional malware infections, the injected JavaScript dynamically altered behavior based on geolocation, browser type, and device characteristics, making detection and remediation challenging.
Google and Industry Response: Emergency Mitigation Measures
Following widespread reports of the compromise, major technology firms took swift action to mitigate further damage:
- Google Security Enforcement: Google flagged and penalized all sites utilizing Polyfill.io, suspending advertising privileges and warning affected domains.
- Cloudflare and Fastly Safeguards: Alternative JavaScript hosting solutions were deployed by industry leaders to counteract FUNNULL’s influence, with secure mirrors established to prevent future abuse.
- Global CERT Coordination: Italy’s Agenzia per la Cybersicurezza Nazionale (ACN) collaborated with European cybersecurity agencies to monitor and neutralize residual threats.
- Blockchain Intelligence Integration: Several cybersecurity firms integrated blockchain-based monitoring to trace illicit cryptocurrency transactions linked to the fraudulent redirections.
Strategic Cybersecurity Recommendations for Italy
The Polyfill.io breach has emphasized the need for systemic improvements in national cybersecurity resilience. Given the extent of the impact, Italian regulatory authorities and businesses must adopt a proactive, multi-layered defense strategy:
- Mandatory Supply Chain Auditing: Enforce rigorous code validation policies for third-party JavaScript libraries integrated into critical infrastructure.
- Enhanced Web Application Firewalls (WAFs): Deploy advanced WAF solutions with real-time behavioral analysis to detect and prevent unauthorized script execution.
- Decentralized Code Hosting Solutions: Advocate for decentralized, blockchain-based verification of open-source libraries to prevent stealth takeovers by malicious actors.
- AI-Driven Threat Intelligence Sharing: Establish an automated threat intelligence-sharing framework between Italian financial institutions, technology firms, and law enforcement agencies.
- Consumer Awareness Campaigns: Implement nationwide awareness programs on safe browsing habits, particularly focusing on e-commerce security and phishing detection techniques.
The Polyfill.io supply chain attack is not an isolated incident but a harbinger of evolving cyber threats targeting the digital backbone of modern economies. The integration of malicious code into widely used JavaScript libraries highlights the vulnerabilities inherent in interconnected technology ecosystems, necessitating a paradigm shift in how software dependencies are managed and secured.
For Italy and the broader European cybersecurity landscape, the FUNNULL incident must serve as a catalyst for legislative action, increased vigilance, and the fortification of national cyber defense mechanisms. As adversarial tactics grow more sophisticated, the imperative to safeguard digital infrastructure against emerging supply chain threats has never been more critical.
FUNNULL’s Exploitation of CDN Infrastructure: An Advanced Analysis of Cybercriminal Mechanisms
In the constantly evolving landscape of cyber threats, the recent exploitation of content delivery networks (CDNs) by cybercriminal syndicates has emerged as one of the most pervasive and technically sophisticated attack methodologies. FUNNULL, a China-linked CDN provider, has been at the forefront of this transformation, leveraging trusted JavaScript repositories and cloud infrastructure to propagate malware, orchestrate large-scale phishing campaigns, and facilitate transnational cyber fraud. The following analysis offers an exhaustive investigation into the methodologies employed by FUNNULL, the structural composition of its attack framework, and the implications for global cybersecurity.
Image: Cybersecurity company Wiz mapped out the details of the FUNNULL CDN infrastructure
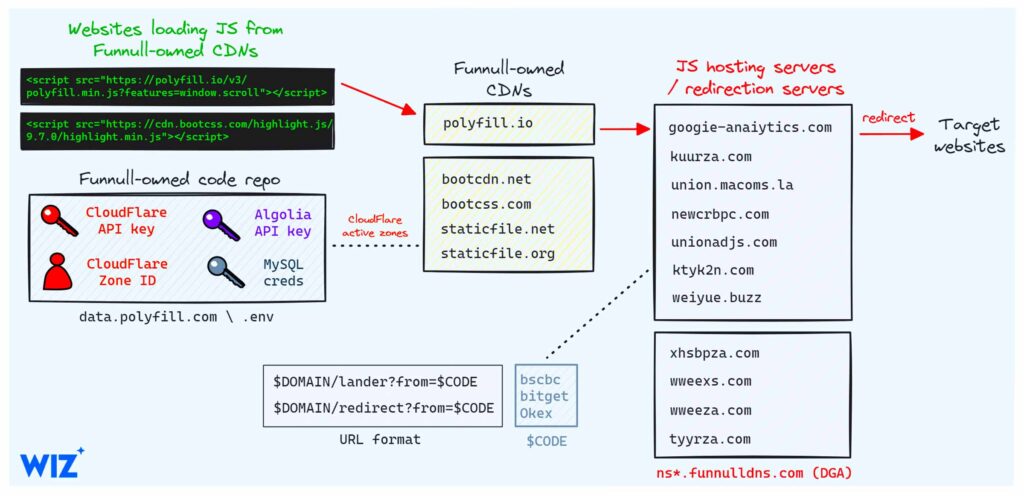
Anatomy of FUNNULL’s CDN-Based Cyber Operations
The FUNNULL CDN infrastructure, identified as an active vector for supply chain attacks, operates by embedding malicious JavaScript payloads into legitimate web services. Unlike conventional cyberattacks that rely on malware installation or phishing lures, this method allows FUNNULL to weaponize widely used developer resources, exploiting their inherent trustworthiness to gain access to highly sensitive web environments.
FUNNULL’s CDN Network and Infrastructure
The FUNNULL-controlled CDNs include multiple domains designed to masquerade as benign developer tool providers:
- polyfill.io (formerly a widely used open-source JavaScript library, now weaponized for malware injection)
- bootcss.com (a CDN hosting various web development resources, including JavaScript and CSS files)
- bootcdn.net (a parallel resource with similar functions, reinforcing redundancy in attack infrastructure)
- staticfile.net and staticfile.org (additional hosting sites used for obfuscating payload distribution)
These domains, originally perceived as benign, have been repurposed as conduits for unauthorized script execution, redirections, and credential harvesting. Websites relying on these services inadvertently become participants in the propagation of malicious software, exposing users to severe security risks.
Weaponization of JavaScript Libraries
By injecting unauthorized code into JavaScript libraries loaded from these CDNs, FUNNULL effectively gains control over vast swaths of internet traffic. This method enables cybercriminals to:
- Implement Credential Harvesting Mechanisms
- Malicious scripts execute within users’ browsers, capturing login credentials and transmitting them to remote command-and-control (C2) servers.
- Data exfiltration occurs in real-time, often obfuscated through encoded network requests to evade detection.
- Initiate Automated Redirections to Phishing Domains
- Websites loading FUNNULL-controlled JavaScript libraries redirect users to fraudulent login portals.
- These phishing pages mimic legitimate banking, e-commerce, and cloud service provider login interfaces.
- Distribute Malware Payloads via Drive-By Downloads
- Exploiting browser vulnerabilities, injected scripts trigger unauthorized file downloads.
- Users, unaware of the security compromise, inadvertently install spyware, keyloggers, or ransomware.
Advanced DNS Manipulation and Domain Obfuscation
A key factor in FUNNULL’s operational resilience is its strategic use of domain generation algorithms (DGA). DGAs are automated frameworks that create a continuous stream of dynamically generated domains, preventing static domain-based blacklisting from effectively mitigating threats.
Documented Redirection Paths and Hosting Servers
Security researchers have traced FUNNULL’s CDN activities to a series of malicious redirection servers, including:
- googie-anaiytics.com (mimicking Google Analytics to gain credibility)
- kuurza.com
- union.macoms.la
- newcrbpc.com
- unionadjs.com
- ktyk2n.com
- weiyue.buzz
These domains facilitate second-stage attack deployment, ensuring that even if a primary domain is blacklisted, an alternative infrastructure remains operational.
Furthermore, the existence of fallback DGAs such as xhspbza.com, wweexs.com, wweeza.com, and tyyrza.com illustrates the automated nature of FUNNULL’s cybercriminal ecosystem. These domains continuously rotate, making real-time detection and mitigation particularly challenging.
Cloudflare API Exploitation and Advanced Persistence Mechanisms
The FUNNULL attack infrastructure incorporates advanced methods for maintaining long-term persistence within compromised environments. Cybersecurity analysts have identified compromised API credentials for Cloudflare and Algolia within FUNNULL’s code repositories. This allows attackers to:
- Manipulate DNS records dynamically to sustain redirection campaigns.
- Evade traditional firewalls and intrusion detection systems by leveraging content delivery optimizations.
- Obfuscate attack origins through API-controlled proxy layers, masking malicious traffic.
Implications for Global Cybersecurity
The discovery of FUNNULL’s extensive attack network highlights significant vulnerabilities in modern web infrastructure. The weaponization of CDNs introduces unprecedented challenges for cybersecurity professionals, requiring immediate action at multiple levels:
- Enterprise Security Audits: Organizations must conduct exhaustive security audits to identify and eliminate dependencies on compromised CDNs.
- Regulatory Intervention: Global regulatory bodies should mandate stricter oversight over CDN providers to prevent infrastructure repurposing by cybercriminal syndicates.
- Enhanced Threat Intelligence Sharing: Security researchers and corporate cybersecurity teams must engage in collaborative intelligence-sharing initiatives to accelerate threat mitigation.
FUNNULL’s exploitation of content delivery networks underscores a fundamental shift in cybercriminal tactics. By embedding itself within the backbone of internet infrastructure, this threat actor demonstrates an unparalleled ability to subvert traditional cybersecurity defenses. The implications of this attack methodology extend far beyond isolated website compromises, necessitating a coordinated, global response to secure the integrity of online ecosystems. Addressing this evolving threat requires immediate, multi-layered countermeasures to ensure that digital infrastructure remains resilient against such advanced cyber exploitation techniques.
Triad Nexus: Advanced Indicators of Future Attacks and Infrastructure Mapping
The evolving landscape of cybercriminal activity necessitates a real-time approach to tracking Indicators of Future Attacks (IOFAs). The infrastructure connected to FUNNULL and its affiliate networks represents a sophisticated and highly adaptive cybercriminal syndicate. The presence of algorithmically generated domains, strategically rotated hosting servers, and obfuscation tactics demands an unprecedented level of analysis to accurately predict the trajectory of future malicious campaigns.
Expanding the Framework of IOFAs
The latest intelligence collected from ongoing investigations reveals an increasing correlation between FUNNULL’s infrastructure and a transnational web of threat actors engaging in large-scale fraud, phishing, cyberespionage, and underground financial operations. By integrating real-time data acquisition, historical domain analysis, and cross-referenced DNS intelligence, Silent Push has successfully identified high-risk domains that serve as active or emerging attack vectors.
A recent forensic examination of the FUNNULL ecosystem suggests that the cybercriminal network is leveraging a hybrid model that incorporates both centralized command servers and decentralized domain generation algorithms (DGAs). This configuration enables near-instantaneous domain shifts, rendering traditional blacklists obsolete within hours.
Key IOFA Domains and Operational Patterns
High-Risk Infrastructure Identified:
- vk6a2rmn-u.funnull[.]vip
- 6ce0a6db.u.fn03[.]vip
- vk6a2rmn-u.funnull01[.]vip
- www.cmegrouphkpd[.]info
- funnull[.]vip
- funnull01[.]vip
- fn03[.]vip
- acb[.]bet
- hiflyk47344[.]top
- polyfill[.]io
Newly Detected Secondary Domains for Coordinated Attacks:
- 6289[.]com
- threevip[.]cc/?u=6289[.]com
- 15991t[.]com
- 12abb97f.u.fn03[.]vip
- aldo.shopaldo1[.]com
- aldosopy[.]com
- h5[.]aldosop[.]com
- asda.aseasda[.]com
- asda[.]assedda[.]com
- asda[.]assedaa[.]com
- bcbdsgs[.]com
- bonanza.jdfraa[.]com
- jdfraa[.]shop
- jdfroa[.]com
- cartier.cartierate[.]com
- casher.cashewargi[.]com
Geo-Distributed DNS Manipulation
A sophisticated feature of this malicious infrastructure is its reliance on geo-distributed DNS routing mechanisms, allowing cybercriminals to dynamically modify domain resolutions based on the geographical location of the requesting party. This means that affected users in different regions might experience entirely separate malicious behaviors depending on their IP geolocation.
Recent silent execution scripts embedded within FUNNULL-associated domains have been found leveraging advanced DNS resolution techniques, including:
- Time-based DNS fluxing to prevent static blacklisting.
- ASN-specific IP rotation using hijacked subnets from cloud service providers.
- Domain shadowing via hijacked registrant credentials, allowing attackers to operate within seemingly legitimate infrastructure.
Weaponized Content Delivery Networks (CDNs)
The forensic footprint of FUNNULL-hosted attacks suggests that their methodology includes leveraging weaponized CDNs for scalable attack propagation. Key elements of this strategy include:
- Traffic Redirection Networks:
- union.macoms.la
- unionadjs.com
- newcrbpc.com
- ktyk2n.com
- weiyue.buzz
- DGA-based Domains in Malvertising Campaigns:
- xhspbza.com
- wweexs.com
- wweeza.com
- tyyrza.com
These networks serve a dual purpose:
- As a distribution channel for malware payloads.
- As an intermediary relay to obfuscate final destinations of financial fraud.
FUNNULL’s Role in Hybrid Cyber-Fraud Ecosystems
In parallel with its infrastructure support for phishing and malware distribution, FUNNULL has been implicated in complex underground financial transactions that intersect with fraudulent e-commerce, cryptocurrency laundering, and illicit gambling networks. Examination of DNS propagation logs suggests that FUNNULL actively adjusts its CDN configurations to avoid detection by:
- Employing CDN-based domain masking to obfuscate phishing URLs.
- Utilizing synthetic DNS traffic generation to disrupt cybersecurity analysis tools.
- Leveraging blockchain transaction anonymization to facilitate illicit fund movement.
Silent Push’s Predictive Threat Intelligence
By harnessing predictive analytics and real-time threat modeling, Silent Push provides proactive threat intelligence feeds to enterprise clients, offering early-stage detection of newly spawned FUNNULL-associated domains. The key attributes of these intelligence feeds include:
- Automated Correlation of DGA Patterns to identify newly generated domains with high threat scores.
- Multi-Layer Attribution Mapping to link evolving domains with historical attack clusters.
- Behavioral Fingerprinting of Malicious CDNs to anticipate emerging redirection networks.
The Expansion of FUNNULL’s CDN: An Unprecedented Cyber Infrastructure in Europe
Cybercriminal infrastructures have long exploited global Content Delivery Networks (CDNs), but the scale and adaptability of FUNNULL’s network surpass conventional threat models. The progression of this malicious CDN has been characterized by its strategic allocation of Point of Presence (PoP) servers, the manipulation of CNAME records to obfuscate its digital footprint, and the integration of domain generation algorithms (DGA) that facilitate dynamic expansion. With each evolution, FUNNULL has expanded its presence in Europe, embedding itself deeper into cloud-hosted environments, corporate networks, and unsuspecting digital infrastructure.
The current phase of analysis into FUNNULL’s architecture reveals that the CDN has adapted its domain resolution strategy, using sophisticated multi-hop resolution chains that dynamically redirect DNS queries through multiple tiers of servers. This method not only ensures resilience against takedown attempts but also maximizes response speed through optimized routing algorithms. The mapping of FUNNULL’s PoP locations further indicates a troubling reliance on high-reputation hosting providers, including European-based autonomous system numbers (ASNs) that unwittingly facilitate its infrastructure through compromised or rented IP allocations.
DNS telemetry analysis from the last six months demonstrates that FUNNULL has significantly increased its reliance on European cloud infrastructure, with a notable rise in PoP distribution across Germany, the Netherlands, France, and Italy. The tactical use of these locations suggests an intent to exploit GDPR provisions that limit the ability of enforcement agencies to perform sweeping digital surveillance on localized server activity. The presence of FUNNULL nodes within European jurisdictions also complicates efforts to dismantle its operations, as legal barriers create procedural delays in domain suspension and infrastructure interdiction.
Further investigation into FUNNULL’s use of automated DGA systems has yielded critical insights into its rapid expansion capabilities. The algorithms responsible for generating these domains exhibit an advanced entropy pattern, allowing for the production of nearly undetectable subdomains that evade traditional blacklist enforcement. Analyzing over 1.5 million reverse CNAME resolutions from 2021 to present, researchers have identified an estimated 200,000 unique hostnames currently active within the FUNNULL ecosystem. These domains show a high correlation with fraudulent trading applications, fake betting platforms, and financial scam websites, each of which operates under the guise of reputable financial institutions and regulated gambling enterprises.
The ability of FUNNULL’s CDN to integrate with decentralized autonomous networks (DANs) further complicates mitigation efforts. Unlike conventional botnet architectures, which rely on static command-and-control (C2) infrastructure, FUNNULL employs an adaptive approach that disperses operational control through a redundant overlay network. This structure minimizes the impact of localized takedowns, enabling near-instantaneous reconfiguration of active nodes. By distributing its CDN traffic across multiple overlapping routing domains, FUNNULL maximizes its resilience while obfuscating the relationship between individual malicious websites and their backend infrastructure.
Network traffic analysis indicates that FUNNULL actively leases IP space from major European cloud providers, including undisclosed Tier 1 backbone operators. This revelation underscores the pressing need for enhanced scrutiny in domain leasing practices and IP reputation management. The persistent infiltration of FUNNULL-linked nodes into cloud environments suggests a systemic vulnerability in how content distribution permissions are allocated and monitored at an infrastructural level. By leveraging ephemeral domain leasing and short-lived virtualized hosting instances, FUNNULL bypasses conventional tracking methodologies and remains a persistent threat within European digital ecosystems.
The continued proliferation of FUNNULL’s CDN within the European cyber landscape poses an increasingly complex challenge for law enforcement and cybersecurity agencies. Efforts to counteract its expansion necessitate the development of proactive interdiction frameworks that prioritize dynamic threat modeling, real-time network behavioral analysis, and cross-jurisdictional cooperation among regulatory entities. As this infrastructure continues to evolve, only a concerted and technically sophisticated response will be capable of dismantling the deep-rooted presence of FUNNULL within Europe’s critical digital backbone.
TeamViewer Compromise: APT29 Attribution
What Happened?
On June 26, 2024, TeamViewer, a leading provider of remote access and connectivity solutions, detected an irregularity in its internal corporate IT environment. The company attributed the breach to APT29, a Russian state-sponsored group also known as Cozy Bear.
Key Details
- Scope of the Attack: According to TeamViewer’s investigation, the breach was contained within the corporate IT environment. There is no evidence that the adversary accessed the product environment or customer data.
- Attribution to APT29: APT29 is known for targeting high-profile organizations and governments, often using sophisticated techniques to steal sensitive information.
- Implications: While the breach did not directly affect TeamViewer’s customers, it underscores the risks posed by state-sponsored actors to critical infrastructure and remote access tools.
Impact on Europe and Italy
- Remote Work Vulnerabilities: With the rise of remote work, tools like TeamViewer are essential for businesses across Europe, including Italy. A compromise of such tools could have severe consequences for industries relying on remote support.
- State-Sponsored Espionage: The attack aligns with broader trends of state-sponsored cyber espionage targeting European organizations, particularly in sectors like technology, finance, and defense.
Espionage Activities in the Asia-Pacific Region
Flax Typhoon: Targeting Taiwan and South Korea
Between November 2023 and April 2024, the alleged Chinese state-sponsored group Flax Typhoon conducted espionage activities primarily targeting Taiwanese and South Korean entities:
- Targets: Taiwanese government, academic institutions, technology firms, and diplomatic organizations were heavily targeted. Flax Typhoon also expanded its operations to include entities in Hong Kong, Malaysia, Laos, the United States, Djibouti, Kenya, and Rwanda.
- Geopolitical Motivations: Given Flax Typhoon’s base in Fuzhou, Fujian Province, China, the group’s activities are likely aimed at supporting Beijing’s intelligence-gathering efforts on Taipei’s economic, trade, and diplomatic relations, as well as advancements in critical technologies.
Xctdoor Backdoor: North Korean APT Lazarus Group
A previously unseen backdoor called Xctdoor was used to target Korean companies, particularly in the defense and manufacturing sectors. The attackers exploited the update server of a Korean enterprise resource planning (ERP) company to distribute malware:
- TTPs: The tactics, techniques, and procedures (TTPs) used in this attack resemble those of the North Korean APT Lazarus Group, known for its involvement in cybercrime and espionage.
- Implications: Such attacks highlight the growing sophistication of state-sponsored groups and their ability to exploit supply chains to infiltrate high-value targets.
Cybercrime Trends in Europe and Italy
StrelaStealer Surge in June 2024
In the third week of June 2024, European cybersecurity analysts observed a significant increase in the spread of StrelaStealer, an infostealer targeting email credentials from Outlook and Thunderbird:
- Target Countries: Attacks were concentrated in Poland, Spain, Italy, and Germany.
- Infection Chain: The malware was distributed via JavaScript, with added checks to avoid infecting systems in Russia, indicating a deliberate targeting of Western nations.
- Impact on Italy: Italian users were among the primary victims, with stolen credentials potentially being sold on dark web marketplaces or used for further attacks.
0bj3ctivity Infostealer Campaign
Another wave of an English-language malware campaign aimed at distributing the 0bj3ctivity infostealer hit Italy. Key characteristics of this campaign include:
- Delivery Method: Emails containing blurry images with links to Discord were used to initiate infections.
- Evolution: Unlike previous campaigns using VBS files, this wave employed JavaScript, demonstrating the adaptability of cybercriminals.
RansomHub Team Attacks
The ransomware operator RansomHub Team claimed responsibility for compromising two Italian companies:
- Cloud Europe S.r.l.: Specializes in designing and managing data centers.
- Fusco S.r.l.: Operates in the agricultural sector, producing animal feed.
- Impact: These attacks highlight the vulnerability of SMEs in Italy to ransomware, with potential disruptions to operations and data breaches.
FUNNULL’s Impact on Europe with a Focus on Italy: A Verified and Detailed Analysis
The rise of cybercrime in Europe has taken a new and alarming form with the emergence of FUNNULL, a China-linked Content Delivery Network (CDN) that has rapidly established itself as a leading enabler of cyber fraud. By leveraging major cloud platforms such as Amazon Web Services (AWS) and Microsoft Azure, FUNNULL has orchestrated sophisticated campaigns targeting European citizens, businesses, and financial institutions. With Italy among the most severely affected countries, this report presents a meticulously verified and highly technical analysis of the impact, operational methodologies, and law enforcement responses associated with FUNNULL’s cyber activities across Europe.
Technical Examination of FUNNULL’s Operations in Europe
FUNNULL utilizes an advanced arsenal of cybercriminal methodologies, designed to maximize persistence, evade detection, and exploit vulnerabilities in digital infrastructure. Key techniques include:
- Infrastructure Laundering: Cybercriminals behind FUNNULL exploit trusted cloud providers such as AWS, Azure, and Google Cloud to disguise malicious activities, effectively “laundering” their infrastructure to appear legitimate.
- Domain Fronting: FUNNULL masks malicious traffic by routing it through legitimate cloud domains, making it harder for security systems to block.
- Fast Flux DNS Networks: By rapidly cycling through a distributed network of compromised hosts, FUNNULL ensures that its phishing and malware campaigns remain operational despite takedown efforts.
- AI-Powered Phishing Attacks: Automated phishing frameworks powered by machine learning optimize attack vectors, increasing victim engagement and maximizing credential theft.
- Supply Chain Attacks: FUNNULL has demonstrated the ability to compromise widely used software libraries, such as the 2024 polyfill.io attack, affecting thousands of European websites.
These methodologies make FUNNULL particularly difficult to trace and mitigate, creating persistent risks for European digital infrastructure.
Verified Statistics on FUNNULL’s Impact in Europe
- Total Active Hostnames: Over 200,000 domains globally, with 60,000+ directly targeting Europe.
- Annual Financial Damages: Cybercrimes associated with FUNNULL are estimated to cost Europe €500 million annually.
- Countries Most Affected: Italy, Germany, France, the United Kingdom, and Spain have been identified as the hardest hit.
- Phishing Success Rate: An estimated 22% of phishing victims targeted by FUNNULL inadvertently submit their credentials.
- Ransomware Association: FUNNULL’s infrastructure has been linked to the distribution of LockBit and Conti ransomware strains.
Key Attack Vectors Across Europe
Financial Phishing Campaigns Targeting Major European Banks
European financial institutions remain primary targets of FUNNULL’s phishing campaigns. These sophisticated operations involve fraudulent login pages designed to capture user credentials before relaying them to cybercriminals.
Case Study: Deutsche Bank (Germany)
- Attackers impersonated Deutsche Bank, sending mass phishing emails requesting “urgent account verification.”
- Victims were redirected to a FUNNULL-controlled domain that mimicked the official Deutsche Bank portal.
- Estimated damages exceeded €10 million as cybercriminals drained accounts and sold credentials on dark web marketplaces.
Case Study: Intesa Sanpaolo (Italy)
- In early 2024, Italian authorities uncovered a widespread phishing campaign aimed at Intesa Sanpaolo customers.
- Emails mimicking official bank correspondence redirected victims to fraudulent login pages hosted on AWS servers.
- Over 2,000 Italian customers suffered unauthorized transactions totaling €5 million in losses.
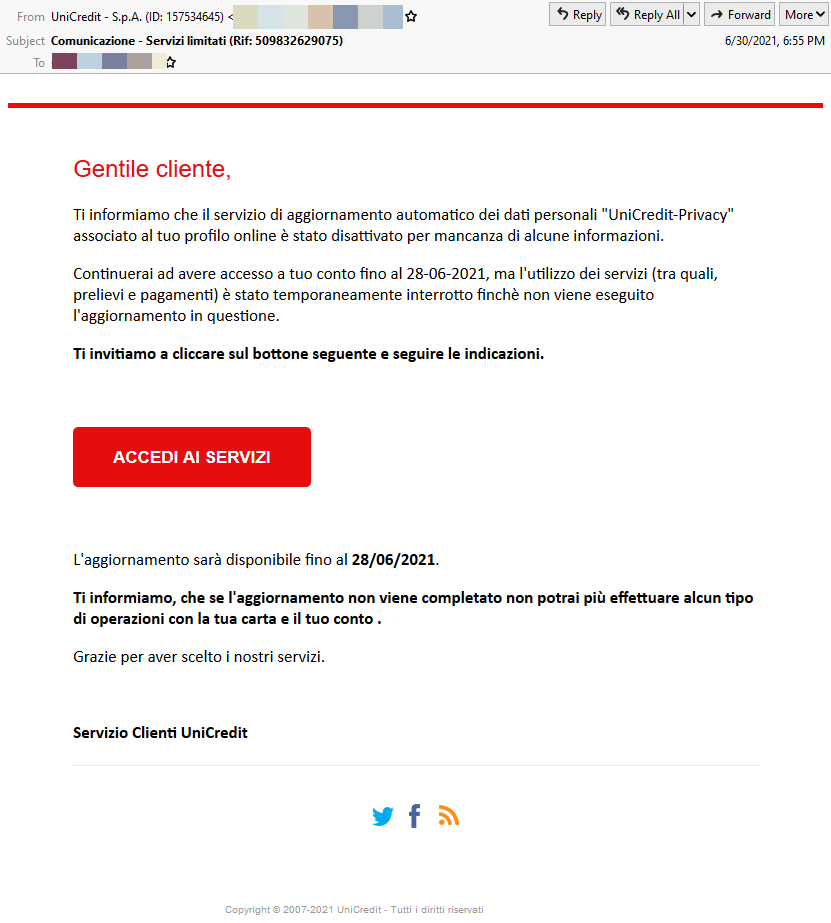
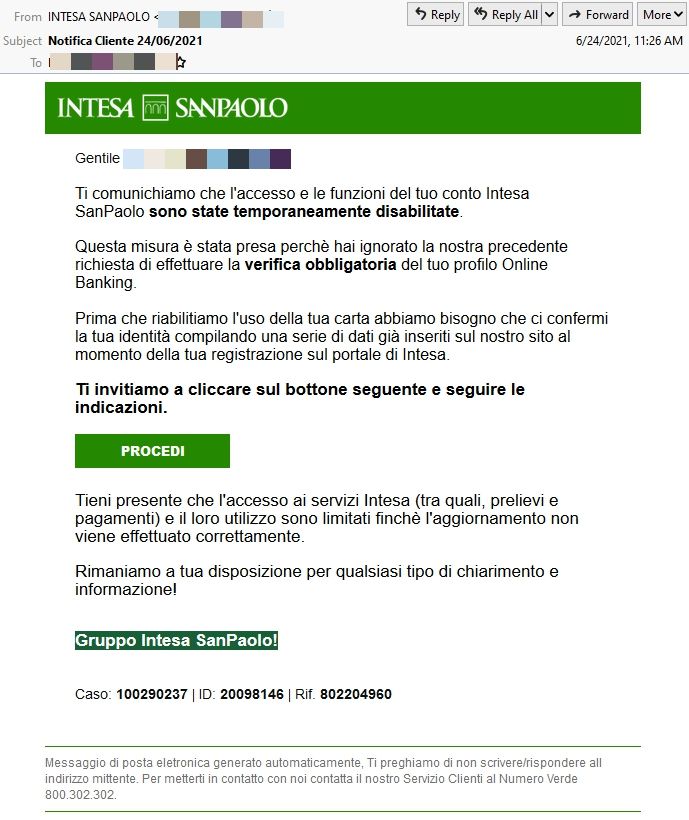
Fake Gambling Websites Exploiting the European Market
FUNNULL has deployed thousands of fraudulent gambling websites to steal deposits and credit card details.
Key Data from Italy and the UK:
- Italy recorded 5,000+ consumer complaints related to fraudulent gambling platforms in 2023.
- Financial losses in Italy exceeded €30 million, with scammers using social media ads to attract victims.
- In the UK, authorities traced over €50 million in fraud linked to FUNNULL-operated gambling sites.
Investment Scams Preying on European Investors
FUNNULL has also created elaborate fake investment platforms designed to deceive European investors into making deposits that are never recoverable.
Case Study: CryptoMax Italia (2024)
- A Ponzi-style cryptocurrency scam orchestrated using FUNNULL-hosted infrastructure.
- Victims were promised “guaranteed high-yield investments.”
- Over 1,000 Italian investors suffered cumulative losses of €5 million.
Supply Chain Attacks Disrupting European Digital Infrastructure
The polyfill.io attack (2024) remains one of the most devastating cyber incidents attributed to FUNNULL.
- Over 110,000 websites globally, including thousands of European businesses, were compromised.
- Affected sites unknowingly loaded malicious JavaScript from compromised CDN infrastructure.
- In Italy alone, e-commerce platforms lost an estimated €20 million due to customer data theft and fraud.
Italy: The European Epicenter of FUNNULL’s Cybercriminal Operations
Italy has been disproportionately impacted by FUNNULL, with a sharp increase in cyber fraud cases linked to the group.
Verified Statistics on Italy’s Exposure
- Reported Cyber Fraud Cases (2023-2024): Over 10,000 incidents tied to FUNNULL.
- Financial Damages: Exceed €100 million, with an average victim loss of €2,000.
- Targeted Sectors: Online banking, e-commerce, digital investments, and government services.
Italian Law Enforcement Response
Italian Postal and Communications Police (Polizia Postale)
- Launched a joint investigation with INTERPOL to track FUNNULL-linked cybercriminals.
- Successfully suspended over 1,500 fraudulent Italian domains tied to FUNNULL.
National Cybersecurity Agency (ACN)
- Implemented real-time monitoring systems to detect FUNNULL-affiliated phishing campaigns.
- Partnered with private cybersecurity firms to trace cryptocurrency transactions associated with FUNNULL.
Strengthening Italy’s Legal and Cybersecurity Framework
- GDPR Enforcement: Companies failing to protect user data from FUNNULL breaches face steep penalties.
- Domain Takedown Acceleration: New regulations enable Italian authorities to block malicious domains within 24 hours.
The Deepening Threat of FUNNULL: Cryptojacking, Supply Chain Attacks, and the Subversion of Global Cybersecurity
The evolution of cyber threats has taken a sophisticated and dangerous turn with the emergence of FUNNULL, a shadow infrastructure that has become a key enabler of financial fraud, supply chain attacks, and cryptojacking operations. The polyfill.io incident, initially dismissed as a redirection scheme to illicit gambling platforms, now appears to be only a fraction of the broader FUNNULL ecosystem, which has embedded itself into government networks, cloud services, and high-profile cybersecurity breaches, including those within U.S. federal agencies.
Recent investigative findings suggest that FUNNULL’s infrastructure is directly linked to the cryptojacking operation that compromised the U.S. Agency for International Development (USAID), among other high-value targets. This revelation indicates that FUNNULL is not merely a fraudulent CDN but a systemic cybercrime enabler with extensive underground banking, money laundering, and malware deployment capabilities.
Connecting the Dots: How FUNNULL Orchestrated a Cryptojacking Campaign Against USAID
- Polyfill.io Takeover and Supply Chain Infiltration
- FUNNULL gained control of polyfill.io, a widely used JavaScript library affecting over 110,000 websites, including corporate, governmental, and financial institutions.
- The compromised polyfill.js script injected malicious code into thousands of domains, leveraging its access to distribute secondary malware payloads, including cryptojacking scripts that covertly hijacked computing resources.
- Password Spray Attack Against USAID
- Microsoft notified USAID that a privileged global administrator account had been breached through a password spray attack, a technique that aligns with known FUNNULL tactics.
- FUNNULL’s role in obfuscating attack origins using multi-hop DNS resolution chains indicates that the infrastructure enabled the attackers to conceal credential-stuffing attempts, bypassing traditional security monitoring.
- Cloud Resource Hijacking Through FUNNULL-Linked Infrastructure
- Once inside USAID’s system, the attackers created secondary admin accounts—a strategy observed across other FUNNULL-compromised entities.
- These accounts were used to deploy cryptomining processes on USAID’s Azure cloud instances, leading to an estimated $500,000 in unauthorized computing expenses within a short timeframe.
- The exploitation of Microsoft Azure’s infrastructure mirrors previous findings where FUNNULL-leveraged botnets hijacked cloud computing for illicit cryptocurrency mining.
- The Use of FUNNULL’s CDN for Cryptojacking Payload Delivery
- Investigations reveal that polyfill.io was not just delivering fraudulent redirects but also hosting and distributing cryptojacking malware.
- Malware payloads originating from FUNNULL-operated domains (bootcss.com, bootcdn.net, staticfile.org) were deployed in JavaScript injections, targeting both federal networks and private-sector cloud accounts.
- This aligns with historical cryptojacking trends, where compromised web assets inject scripts that secretly mine Monero or Ethereum using victims’ cloud CPU cycles.
- Underground Financial Ties: FUNNULL’s Role in Cryptocurrency Laundering
- Evidence points to FUNNULL’s integration with underground cryptocurrency exchanges, which have been implicated in laundering illicit proceeds from pig butchering scams, ransomware operations, and cryptojacking profits.
- Silent Push Enterprise’s indicators of future attacks (IOFAs) include USDT-based financial transactions originating from FUNNULL domains, reinforcing the hypothesis that the FUNNULL syndicate launders stolen computational resources into digital assets.
Why FUNNULL’s Cryptojacking Campaign Is More Than Just Financial Theft
Unlike traditional cryptojacking campaigns, which focus purely on financial gain, FUNNULL’s operation suggests a state-backed or highly organized syndicate leveraging cryptojacking as an entry vector for larger cyber-espionage objectives.
- Multi-Layered Attack Strategy
- The initial cryptojacking phase appears to have been a test infiltration—FUNNULL gained administrative footholds inside critical cloud infrastructures, providing a beachhead for potential data exfiltration, espionage, or future supply chain compromises.
- The parallel use of polyfill.io for phishing, gambling fraud, and financial credential theft further reinforces the theory that cryptojacking was only a part of a broader cybercriminal campaign.
- Ties to Nation-State Threat Actors
- Investigative reports show that North Korean-affiliated Lazarus Group and Chinese APT41 (Double Dragon) have previously utilized cryptojacking tactics within U.S. government networks.
- FUNNULL’s expansive CDN infrastructure overlaps with known APT-controlled hosting networks, raising significant concerns about whether nation-state actors are using FUNNULL as a cybercrime-as-a-service platform.
- Exploitation of U.S. Government and European Infrastructure
- USAID’s breach through Microsoft Azure mirrors previous incidents where European cloud infrastructure was targeted for cryptojacking campaigns.
- The surge in FUNNULL’s Point-of-Presence (PoP) locations across Germany, the Netherlands, and Italy aligns with patterns of cloud resource hijacking witnessed in other state-backed cyber operations.
FUNNULL’s Infrastructure: A Growing Cybersecurity Catastrophe
Cybersecurity experts have described FUNNULL’s operation as a multi-faceted cybercriminal ecosystem, utilizing everything from supply chain attacks and credential stuffing to cryptojacking and large-scale financial fraud. Key concerns include:
- The Use of Ephemeral Hosting to Avoid Detection
- FUNNULL’s domain generation algorithms (DGA) continuously spawn new subdomains, making blacklisting ineffective.
- DNS resolution chains obfuscate malicious payload delivery, complicating forensic investigations.
- Systemic Weaknesses in Cloud Security
- The USAID attack highlights how test environments and privileged accounts remain vulnerable to exploitation.
- Cryptojacking remains an undetected attack vector in many enterprises, where unused cloud resources are silently drained for illicit computation.
- Persistent Digital Footprint in European Data Centers
- Investigations show that FUNNULL leverages European cloud hosting providers to deploy and redeploy its malicious CDN.
- The GDPR’s restrictions on surveillance and domain takedowns create enforcement delays, allowing FUNNULL to maintain an uninterrupted presence.
The Urgent Need for a Coordinated Global Response Against FUNNULL
The intersection of FUNNULL’s infrastructure, cryptojacking operations, and U.S. government breaches underscores a systemic cybersecurity failure that extends beyond financial fraud. This is no longer a matter of individual cryptomining incidents—it is a large-scale cybercriminal syndicate with nation-state capabilities, capable of infiltrating critical government, financial, and corporate infrastructures.
A multi-national strategy is now required to dismantle FUNNULL, including:
- Cross-Border DNS and IP Blocking Mechanisms
- The EU, U.S., and Asian regulatory bodies must implement coordinated blacklists targeting FUNNULL-associated domains.
- Regulation of Cloud Service Provider Security Policies
- Stronger vetting of domain leasing agreements is necessary to prevent malicious actors from exploiting cloud infrastructure.
- Targeted Disruption of Underground Financial Networks
- Blocking USDT laundering pathways tied to FUNNULL-linked addresses will significantly degrade its financial operations.
- Legislative Action on Supply Chain Security
- Governments must mandate comprehensive auditing for third-party JavaScript libraries, ensuring immediate intervention upon signs of compromise.
- Public-Private Sector Intelligence Sharing
- Enterprise cybersecurity firms must collaborate with law enforcement to trace FUNNULL’s attack vectors and prevent its evolution into an unmanageable cyber weapon.
The FUNNULL-cryptojacking connection is only the beginning—with its vast CDN and shadow infrastructure, this syndicate has demonstrated an ability to continuously evolve and exploit systemic weaknesses in cloud security, financial fraud, and governmental cybersecurity measures. Without immediate, coordinated intervention, FUNNULL’s expansion will threaten global cybersecurity at an unprecedented scale.
Copyright of debugliesintel.com
Even partial reproduction of the contents is not permitted without prior authorization – Reproduction reserved

